BrandPost: Scary Cyber Threats and Sweet Solutions
CSO Magazine
OCTOBER 26, 2021
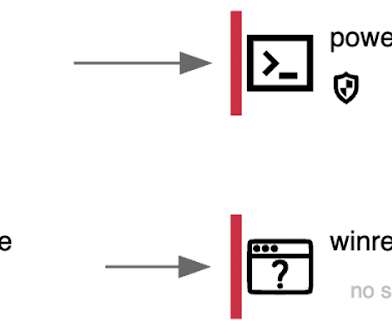
These are the names of top malware that could be haunting your programs and email right now! Building a cyber defense plan may seem scary. What is even scarier: Not having systems in place to protect against malware and other cyber threats. Cyber Threats That Frighten Even The Experts. They should.













Let's personalize your content