Recognising Scam Patterns and Preventing Data Loss: A Unified Approach
IT Security Guru
NOVEMBER 20, 2023
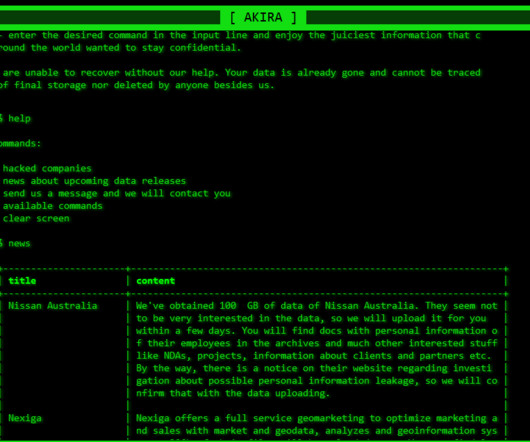
The predictions are on their side, as more intense and frequent cyber attacks will drive up costs by 15% per year. They must recognise the scam patterns that may threaten a business’s data and take a unified approach to prevent data loss and mitigate cyber threats.

















































Let's personalize your content