ThreatDown EDR update: Streamlined Suspicious Activity investigation
Malwarebytes
FEBRUARY 20, 2024
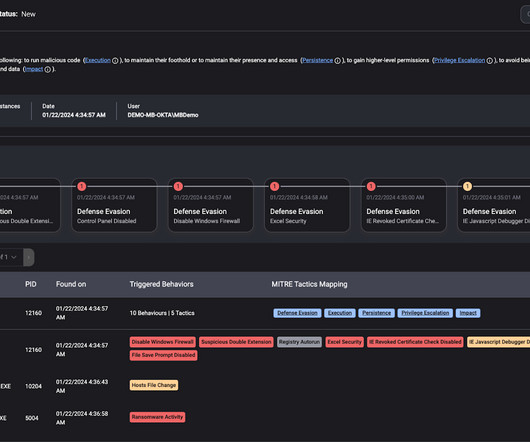
Incident Summary and Timeline updates ThreatDown EDR’s enhancements include two key features: an incident summary that cuts through the jargon and an interactive timeline for a clearer understanding of each alert. The incident summary translates the complex strategies and objectives of cyber threats in straightforward terms.











Let's personalize your content