Mirai-based DDoS botnet IZ1H9 added 13 payloads to target routers
Security Affairs
OCTOBER 11, 2023
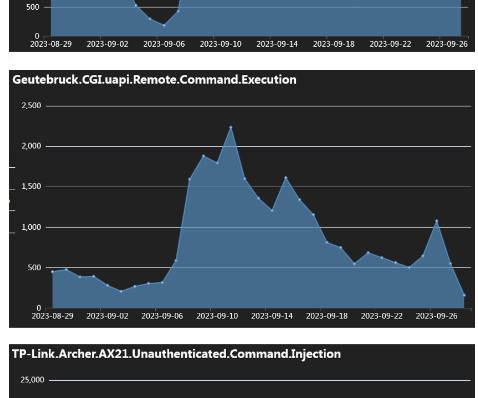
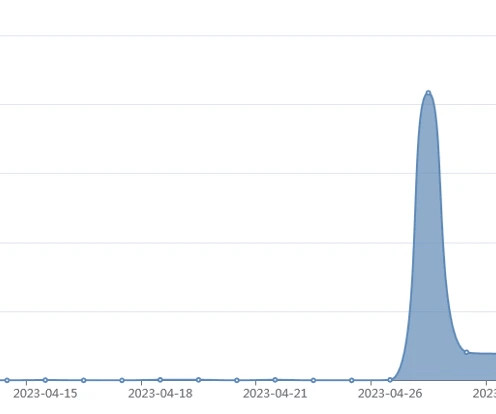
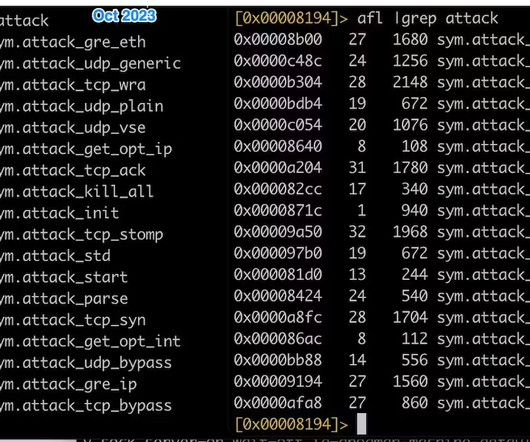
A Mirai-based DDoS botnet tracked as IZ1H9 has added thirteen new exploits to target routers from different vendors, including D-Link, Zyxel, and TP-Link. The botnet supports multiple DDoS attacks, including UDP, HTTP Flood, UDP Plain, and TCP SYN. ” reads the analysis published by Fortinet. ” concludes the analysis.















Let's personalize your content