Experts link the Black Basta ransomware operation to FIN7 cybercrime gang
Security Affairs
NOVEMBER 3, 2022
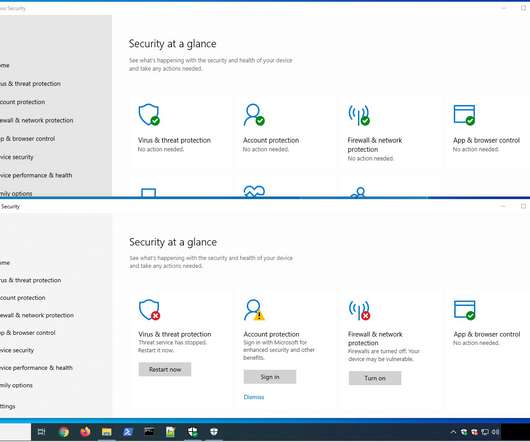
It focused on deploying POS malware and launching targeted spear-phishing attacks against organizations worldwide. In order to weaken the security defenses installed on the target machine, Black Basta targets installed security solutions with specific batch scripts downloaded into the Windows directory.


















Let's personalize your content