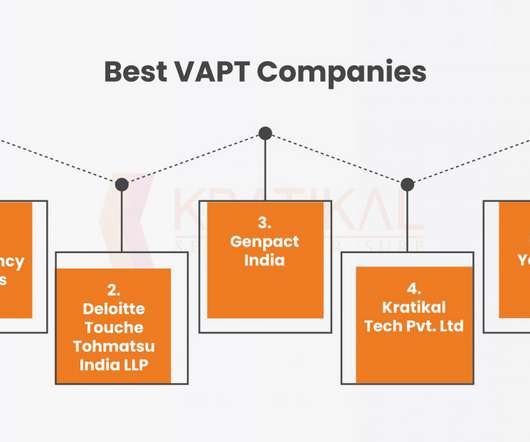
Top VAPT Testing Companies
Security Boulevard
JANUARY 6, 2023
Introduction By reducing information risks and vulnerabilities, a process called information security, also referred to as infosec, protects electronic data. Data collection, organization, processing, and deletion are all included in the definition of data management. InfoSec […].














Let's personalize your content