Cybersecurity Is Not A One-Stop-Shop
Security Boulevard
MAY 6, 2021
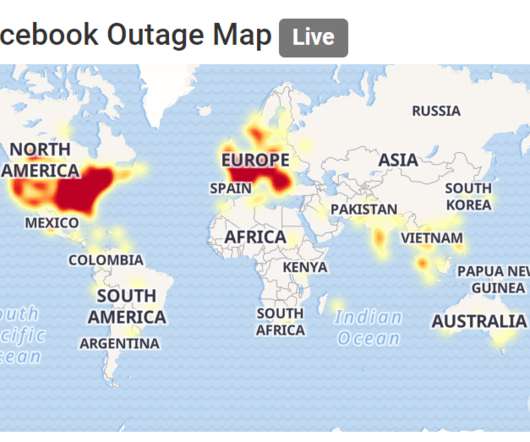
As indoor spaces begin to open in the next few months, employees will want to venture out to new spaces to work, such as coffee shops and internet cafes – but working on open networks and personal devices creates unlocked gateways for cyberattacks to take place. DNS is frequently targeted by. DNS is frequently targeted by.





















Let's personalize your content