Book Review: 'If It’s Smart, It’s Vulnerable'
Lohrman on Security
SEPTEMBER 25, 2022
This review covers Mikko Hypponen’s latest book, If It’s Smart, It’s Vulnerable. This is an excellent book that is highly recommended.

Lohrman on Security
SEPTEMBER 25, 2022
This review covers Mikko Hypponen’s latest book, If It’s Smart, It’s Vulnerable. This is an excellent book that is highly recommended.
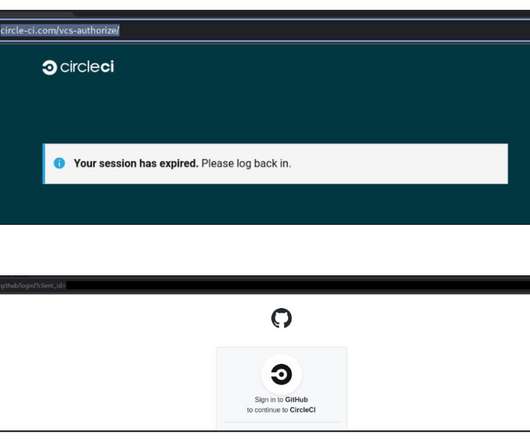
Security Affairs
SEPTEMBER 25, 2022
Threat actors target GitHub users to steal credentials and two-factor authentication (2FA) codes by impersonating the CircleCI DevOps platform. GitHub is warning of an ongoing phishing campaign targeting its users to steal credentials and two-factor authentication (2FA) codes by impersonating the CircleCI DevOps platform. The company learned of the attacks against its users on September 16, it pointed out that the phishing campaign has impacted many victim organizations except GitHub.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

eSecurity Planet
SEPTEMBER 25, 2022
For years the tech industry has promised a shift toward a passwordless future. In 2013, for example, the FIDO Alliance was created to solve the world’s password problem by replacing login technology. Google, Paypal, and Lenovo were among the original FIDO founding members. By 2015, Microsoft joined, and in 2020, Apple followed. The road to a passwordless world has been slow, but seems to have accelerated in the past year, helped in part by Microsoft’s move to passwordless sign-on.

ZoneAlarm
SEPTEMBER 25, 2022
Online scams have become so common that we are immediately suspicious whenever we see a pop-up on a website, get an email with a link to click, or a file to open. So how is it possible that so many people and organizations continue to fall for whatever cybercriminals throw their way? Throughout the hundreds … The post What Does Social Engineering Have to Do with Ransomware?

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Affairs
SEPTEMBER 25, 2022
The Internet Systems Consortium (ISC) fixed six remotely exploitable vulnerabilities in the BIND DNS software. The Internet Systems Consortium (ISC) this week released security patches to address six remotely exploitable vulnerabilities in BIND DNS software. Four out of six flaws, all denial-of-service (DoS) issue, have been rated as ‘high’ severity.

Bleeping Computer
SEPTEMBER 25, 2022
Windows 11 22H2 was just released, and with it comes a new security feature called Enhanced Phishing Protection that warns users when they enter their Windows password in insecure applications or on websites. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
SEPTEMBER 25, 2022
Security analysts at ASEC have discovered a new wave of attacks targeting vulnerable Microsoft SQL servers, involving the deployment of a ransomware strain named FARGO. [.].

Security Affairs
SEPTEMBER 25, 2022
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs free for you in your email box. If you want to also receive for free the newsletter with the international press subscribe here. ISC fixed high-severity flaws in the BIND DNS software Ukraine: SSU dismantled cyber gang that stole 30 million accounts London Police arrested a teen suspected to be behind Uber, Rockstar Games breaches Sophos warns of a new actively exploited fla

WIRED Threat Level
SEPTEMBER 25, 2022
Plus: A leaked trove illuminates Russia’s internet regulator, a report finds Facebook and Instagram violated Palestinian rights, and more.

Bleeping Computer
SEPTEMBER 25, 2022
A previously unknown threat actor that researchers have named 'Metador' has been breaching telecommunications, internet services providers (ISPs), and universities for about two years. [.].

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

WIRED Threat Level
SEPTEMBER 25, 2022
Many companies have pulled physical servers from the country as a mandate to collect customer data goes into effect.

Naked Security
SEPTEMBER 25, 2022
Is this the same suspect as before? Is he part of LAPSUS$? Is this the man who hacked Uber and Rockstar? And, if so, who else?

Bleeping Computer
SEPTEMBER 25, 2022
Data exfiltration malware known as Exmatter and previously linked with the BlackMatter ransomware group is now being upgraded with data corruption functionality that may indicate a new tactic that ransomware affiliates might switch to in the future. [.].

Security Affairs
SEPTEMBER 25, 2022
OpIran: Anonymous launched Operation Iran against Teheran due to the ongoing crackdown on dissent after Mahsa Amini’s death. Anonymous launched OpIran against Iran due to the ongoing crackdown on dissent after Mahsa Amini’s death. The protests began after the death of Mahsa Amini from Saqqez in Kurdistan province after her arrest by Iran’s morality police for allegedly wearing her hijab too loosely.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Bleeping Computer
SEPTEMBER 25, 2022
American Airlines says its Cyber Security Response Team found out about a recently disclosed data breach from the targets of a phishing campaign that was using an employee's hacked Microsoft 365 account. [.].
Let's personalize your content