What Is Patch Tuesday? Microsoft’s Monthly Update Explained
Tech Republic Security
JANUARY 1, 2025
Patch Tuesday is Microsofts monthly update day for fixing vulnerabilities. Learn its purpose, benefits, and how it enhances system security.

Tech Republic Security
JANUARY 1, 2025
Patch Tuesday is Microsofts monthly update day for fixing vulnerabilities. Learn its purpose, benefits, and how it enhances system security.

Security Affairs
JANUARY 1, 2025
The U.S. Treasury sanctioned entities for disinformation tied to Russian and Iranian intelligence before the 2024 presidential elections. The U.S. Treasury sanctioned entities for spreading disinformation linked to Russian and Iranian intelligence ahead of the 2024 presidential elections. The U.S. Treasury sanctioned Moscow’s Center for Geopolitical Expertise (CGE), founded by OFAC-designated Aleksandr Dugin, for spreading disinformation and creating deepfakes ahead of the 2024 elections.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
JANUARY 1, 2025
As we look ahead to 2025, various predictions about the future of cyber threats have been circulating. To bring clarity, we leveraged Googles notebookLLM to summarize key insights from multiple sources about what organizations should prepare for in the coming year and beyond. Heres what you need to know: 1. AI-Driven Cyberattacks Artificial Intelligence (AI) [] The post Key Cyber Threats to Watch in 2025 appeared first on CybeReady.
Penetration Testing
JANUARY 1, 2025
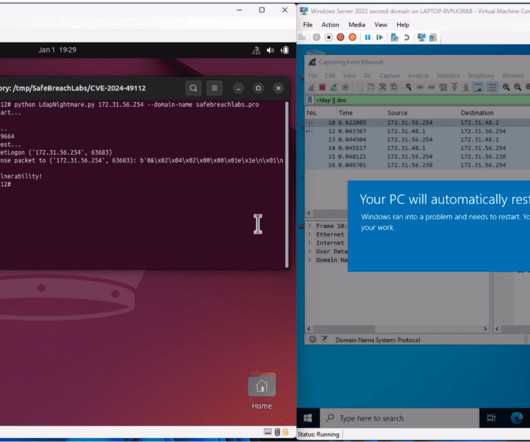
SafeBreach Labs revealed a zero-click vulnerability in the Windows Lightweight Directory Access Protocol (LDAP) service, dubbed LDAP Nightmare. The post PoC Exploit Released for Zero-Click Vulnerability CVE-2024-49112 in Windows appeared first on Cybersecurity News.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Boulevard
JANUARY 1, 2025
Despite years of security awareness training, close to half of businesses say their employees wouldnt know what to do if they received a phishing email. According to a US government-backed study, one of the main reasons for the lack of impact of cyber security training is waning engagement and growing indifference. Why are traditional security [] The post Combatting the Security Awareness Training Engagement Gap appeared first on CybeReady.
The Hacker News
JANUARY 1, 2025
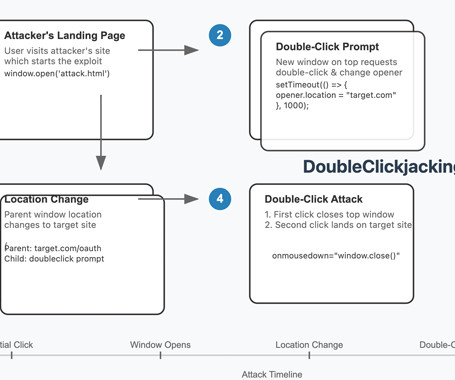
Threat hunters have disclosed a new "widespread timing-based vulnerability class" that leverages a double-click sequence to facilitate clickjacking attacks and account takeovers in almost all major websites. The technique has been codenamed DoubleClickjacking by security researcher Paulos Yibelo. "Instead of relying on a single click, it takes advantage of a double-click sequence," Yibelo said.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Penetration Testing
JANUARY 1, 2025
TRAC Labs has released an in-depth report on LegionLoader, a sophisticated downloader malware that has evolved significantly since The post From Fake Installers to Stolen Credentials: Decoding the LegionLoader Threat appeared first on Cybersecurity News.

Security Boulevard
JANUARY 1, 2025
SafeBreach researchers developed a zero-click PoC exploit that crashes unpatched Windows Servers using the Windows Lightweight Directory Access Protocol (LDAP) remote code execution vulnerability (CVE-2024-49112). The post LDAPNightmare: SafeBreach Labs Publishes First Proof-of-Concept Exploit for CVE-2024-49112 appeared first on SafeBreach. The post LDAPNightmare: SafeBreach Labs Publishes First Proof-of-Concept Exploit for CVE-2024-49112 appeared first on Security Boulevard.

The Hacker News
JANUARY 1, 2025
The U.S. Treasury Department's Office of Foreign Assets Control (OFAC) on Tuesday leveled sanctions against two entities in Iran and Russia for their attempts to interfere with the November 2024 presidential election.

Security Boulevard
JANUARY 1, 2025
Is Your Organizations Trust in Cloud Technology Well-Placed? In this expanding digital landscape where businesses are heavily reliant on cloud technology, can we confidently assert that our data is safe in the cloud? Regardless of the size of your business, trust in cloud platforms should be reinforced. It is a misconception that simply shifting your [] The post Trustworthy Cloud Platforms: Ensuring Secure Access appeared first on Entro.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Hacker's King
JANUARY 1, 2025
In today's world, social media platforms like Twitter have become a huge part of our lives as we keep them updated about ourselves. We can even find some key information about anyone on these platforms. We use Twitter, which can be defined as a famous social media platform and microblogging service that we use to share small messagestweetsto keep everyone updated.

The Hacker News
JANUARY 1, 2025
German prosecutors have charged three Russian-German nationals for acting as secret service agents for Russia. The individuals, named Dieter S., Alexander J., and Alex D., have been accused of working for a foreign secret service. Dieter S. is also alleged to have participated in sabotage operations as well as taking pictures of military installations with an aim to endanger national security.

Security Boulevard
JANUARY 1, 2025
Lets face it: most of us dislike bureaucracy. The endless forms, the rigid processes, and the perceived complexity. Why cant things be simpler? we often ask, blaming bureaucratic systems for complicating everything. However, sometimesperhaps even oftenbureaucracy has its merits. It provides logic, structure, and safeguards that are invaluable, particularly in todays threat landscape.
The Hacker News
JANUARY 1, 2025
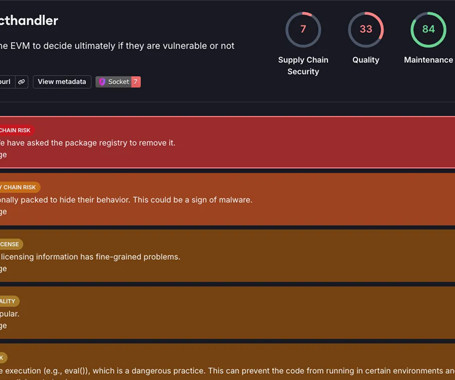
Cybersecurity researchers have discovered a malicious package on the npm package registry that masquerades as a library for detecting vulnerabilities in Ethereum smart contracts but, in reality, drops an open-source remote access trojan called Quasar RAT onto developer systems.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Boulevard
JANUARY 1, 2025
Are You Truly Harnessing the Power of NHIDR Solutions? Its no secret that Non-Human Identities and Data Rights (NHIDR) solutions are crucial for maintaining a robust security system, particularly where cloud environments are involved. But do you fully grasp the potential that these tools can offer when it comes to empowering your team and taking [] The post Take Control: Empowering Your Team with NHIDR Solutions appeared first on Entro.

Zero Day
JANUARY 1, 2025
If you like your Android home screen to give you quick access to information, services, and apps, consider adding a small collection of these widgets.

Security Boulevard
JANUARY 1, 2025
Why Should We Manage Non-Human Identities and Secrets? Imagine a bustling international airport with countless travelers moving in every direction. Now, consider these travelers as your non-human identities (NHIs), each carrying a unique passport (the Secret). The airport, in this case, represents your cloud environment. To ensure a secure, smooth journey for every passenger, would [] The post Feel Reassured with Advanced Identity and Access Management appeared first on Entro.

Penetration Testing
JANUARY 1, 2025
D-Link has issued a critical advisory urging users to retire and replace several legacy router models, including the The post D-Link Issues Warning on End-of-Life Routers Vulnerable to Botnet Exploits appeared first on Cybersecurity News.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Security Boulevard
JANUARY 1, 2025
The post Happy New Year 2025 appeared first on Security Boulevard.

Penetration Testing
JANUARY 1, 2025
Progress Software Corporation, a global provider of products to develop, deploy, and manage high-impact business applications, has issued The post CVE-2024-12108 (CVSS 9.6) and Beyond: Progress Issues Critical Patch for WhatsUp Gold Network Monitoring Software appeared first on Cybersecurity News.

Security Affairs
JANUARY 1, 2025
HHS OCR proposed updates to the HIPAA Security Rule to boost cybersecurity for electronic protected health information (ePHI). On December 27, 2024, the United States Department of Health and Human Services’ (HHS) Office for Civil Rights (OCR) proposed updates to the HIPAA Security Rule to enhance cybersecurity for electronic protected health information (ePHI).

Penetration Testing
JANUARY 1, 2025
Researchers at Unit 42 have discovered a new technique, dubbed “Bad Likert Judge,” that can bypass the safety The post New Research Reveals a Novel “Bad Likert Judge” Technique to Jailbreak LLMs appeared first on Cybersecurity News.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Hacker's King
JANUARY 1, 2025
Table of Contents Introduction: Why Resetting Your Router Password Matters Signs You Need to Reset Your Router Password Steps to Reset Router Password Using the Admin Panel Performing a Factory Reset Common Issues and Troubleshooting Tips to Create a Strong, Secure Password How to Prevent Unauthorized Access Conclusion: Regain Control of Your Router Security Introduction: Why Resetting Your Router Password Matters Have you been wondering, How to reset my router password?

Security Boulevard
JANUARY 1, 2025
Dear blog readers, In this post I'll post some recent actionable intelligence on the Koobface botnet's master Leded (Ded Mazai) and Anton Nikolaevich Korotchenko ( ) Koobface Botnet Master KrotReal. Leded primary email address account: mrpinkesq@yahoo.com Primary domain: hxxp://moblave.com; hxxp://mobpaty.com Related domain registrations: hxxp://xmob-erotic.com hxxp://xerotic-mob.com hxxp://kinozal3d.com hxxp://mob-vids.com hxxp://mob-dating.net hxxp://mob-dating.com hxxp://mob-dating.org hxxp:
Let's personalize your content