Where Next for States on All Things IT and Security?
Lohrman on Security
OCTOBER 15, 2023
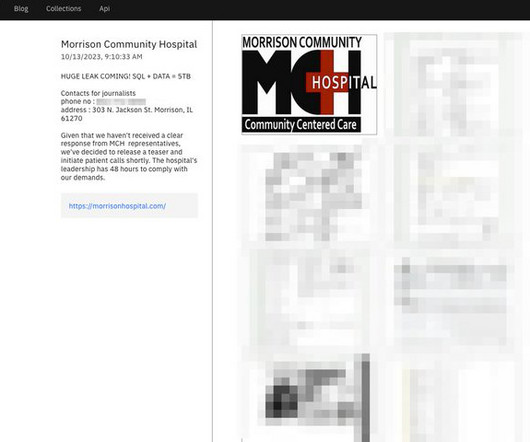
The 2023 NASCIO Annual Conference wrapped up this past week in Minneapolis. Here's a quick roundup of what happened and what’s next for state IT and cybersecurity.
















Let's personalize your content