Windows Kernel EoP Vulnerability (CVE-2024-21345) Gets PoC Exploit Code
Penetration Testing
APRIL 27, 2024
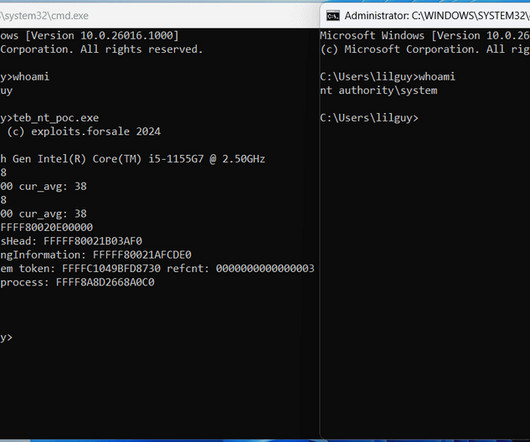
Security researcher Gabe Kirkpatrick has released proof-of-concept (PoC) exploit code for CVE-2024-21345, a high-severity Windows Kernel Elevation of Privilege vulnerability. This exploit allows authenticated attackers to escalate privileges to the SYSTEM level, granting them... The post Windows Kernel EoP Vulnerability (CVE-2024-21345) Gets PoC Exploit Code appeared first on Penetration Testing.























Let's personalize your content