AI Voice Scam
Schneier on Security
MAY 1, 2024
Scammers tricked a company into believing they were dealing with a BBC presenter. They faked her voice, and accepted money intended for her.

Schneier on Security
MAY 1, 2024
Scammers tricked a company into believing they were dealing with a BBC presenter. They faked her voice, and accepted money intended for her.

Tech Republic Security
MAY 1, 2024
Are virtual private networks legal to use? Discover if VPNs are legal, restricted or banned in your geolocation and what activities are legal vs. illegal when using a VPN.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
MAY 1, 2024
At the close of 2019, API security was a concern, though not necessarily a top priority for many CISOs. Related: GenAI ignites 100x innovation Then Covid 19 hit, and API growth skyrocketed, a trajectory that only steepened when Generative AI ( GenAI ) and Large Language Models ( LLMs ) burst onto the scene. As RSA Conference 2024 gets underway next week at San Francisco’s Moscone Center, dealing with the privacy and security fall out of those back-to-back disruptive developments will command a l

Bleeping Computer
MAY 1, 2024
Cloud storage firm DropBox says hackers breached production systems for its DropBox Sign eSignature platform and gained access to authentication tokens, MFA keys, hashed passwords, and customer information. [.

Advertisement
They say a defense can be measured by its weakest link. In your cybersecurity posture, what––or who––is the weakest link? And how can you make them stronger? This webinar will equip you with the resources to search for quality training, implement it, and improve the cyber-behaviors of your workforce. By the end of the hour, you will feel empowered to improve the aspects of your security posture you control the least – the situational awareness and decision-making of your workforce.

Security Boulevard
MAY 1, 2024
Venafi today launched an initiative to help organizations prepare to implement and manage certificates based on the Transport Layer Security (TLS) protocol. The post Venafi Launches 90-Day TLS Certificate Renewal Initiative appeared first on Security Boulevard.
Bleeping Computer
MAY 1, 2024
A new malware named 'Cuttlefish' has been spotted infecting enterprise-grade and small office/home office (SOHO) routers to monitor data that passes through them and steal authentication information. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MAY 1, 2024
HPE Aruba Networking has issued its April 2024 security advisory detailing critical remote code execution (RCE) vulnerabilities impacting multiple versions of ArubaOS, its proprietary network operating system. [.

The Hacker News
MAY 1, 2024
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited Vulnerabilities (KEV) catalog, owing to active exploitation in the wild. Tracked as CVE-2023-7028 (CVSS score: 10.

Bleeping Computer
MAY 1, 2024
Panda Restaurant Group, the parent company of Panda Express, Panda Inn, and Hibachi-San, disclosed a data breach after attackers compromised its corporate systems in March and stole the personal information of an undisclosed number of individuals. [.
Security Affairs
MAY 1, 2024
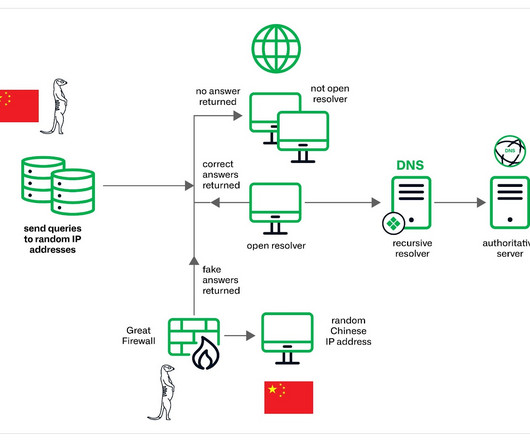
The China-linked threat actors Muddling Meerkat are manipulating DNS to probe networks globally since 2019. Infoblox researchers observed China-linked threat actors Muddling Meerkat using sophisticated DNS activities since 2019 to bypass traditional security measures and probe networks worldwide. The experts noticed a spike in activity observed in September 2023.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Bleeping Computer
MAY 1, 2024
Microsoft has confirmed customer reports of NTLM authentication failures and high load after installing last month's Windows Server security updates. [.
The Hacker News
MAY 1, 2024
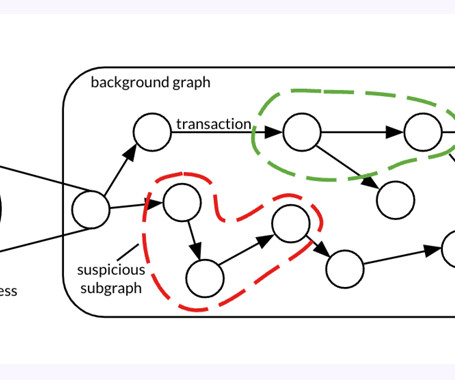
A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market.

Bleeping Computer
MAY 1, 2024
Microsoft says the April 2024 Windows security updates break VPN connections on Windows 11, Windows 10, and Windows Server systems. [.

The Hacker News
MAY 1, 2024
Cybersecurity researchers have discovered a previously undocumented malware targeting Android devices that uses compromised WordPress sites as relays for its actual command-and-control (C2) servers for detection evasion. The malware, codenamed Wpeeper, is an ELF binary that leverages the HTTPS protocol to secure its C2 communications.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Bleeping Computer
MAY 1, 2024
The US government is warning that pro-Russian hacktivists are seeking out and hacking into unsecured operational technology (OT) systems used to disrupt critical infrastructure operations. [.

Penetration Testing
MAY 1, 2024
Security researchers at Lumen Technologies’ Black Lotus Labs have uncovered a sophisticated new malware campaign targeting enterprise-grade small office/home office (SOHO) routers. Dubbed “Cuttlefish,” the malware is designed to remain undetected while stealing sensitive... The post New Cuttlefish Malware Evades Detection, Targets SOHO Routers appeared first on Penetration Testing.

Security Affairs
MAY 1, 2024
Panda Restaurant Group disclosed a data breach that occurred in March, resulting in the theft of associates’ personal information. Panda Restaurant Group disclosed a data breach that occurred in March, resulting in the theft of personal information belonging to its associates. Panda Restaurant Group , Inc. is the parent company of Panda Inn, Panda Express and Hibachi-San.

Penetration Testing
MAY 1, 2024
Recently, HPE Aruba Networking announced a comprehensive update to its ArubaOS software, targeting multiple critical vulnerabilities that could potentially allow attackers to execute arbitrary code remotely and cause denial-of-service conditions. The advisory details patches... The post HPE Aruba Networking Patches Critical Vulnerabilities in Mobility Controllers and Gateways appeared first on Penetration Testing.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
MAY 1, 2024
The RSA Conference 2024 will kick off on May 6. Known as the “Oscars of Cybersecurity,” the RSAC Innovation Sandbox has become a benchmark for innovation in the cybersecurity industry. Today, let’s get to know the company P0 Security. Introduction of P0 Security P0 Security was established in California in 2022. The company provides services […] The post RSAC 2024 Innovation Sandbox | P0 Security’s Cloud Access Governance Platform appeared first on NSFOCUS, Inc., a global network and cyber
The Hacker News
MAY 1, 2024
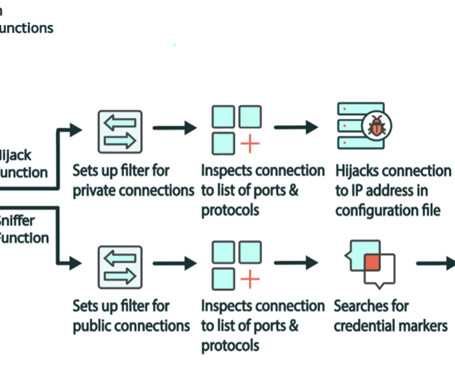
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from HTTP GET and POST requests.

Bleeping Computer
MAY 1, 2024
Qantas Airways confirms that some of its customers were impacted by a misconfiguration in its app that exposed sensitive information and boarding passes to random users. [.

The Hacker News
MAY 1, 2024
The authors behind the resurfaced ZLoader malware have added a feature that was originally present in the Zeus banking trojan that it's based on, indicating that it's being actively developed. "The latest version, 2.4.1.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Bleeping Computer
MAY 1, 2024
The Hôpital de Cannes - Simone Veil (CHC-SV) in France announced it received a ransom demand from the Lockbit 3.0 ransomware gang, saying they refuse to pay the ransom. [.

Security Affairs
MAY 1, 2024
A flaw in the R programming language enables the execution of arbitrary code when parsing specially crafted RDS and RDX files. A vulnerability, tracked as CVE-2024-27322 (CVSS v3: 8.8), in the R programming language could allow arbitrary code execution upon deserializing specially crafted R Data Serialization (RDS) or R package files (RDX). R is an open-source programming language widely used for statistical computing and graphics.

Penetration Testing
MAY 1, 2024
Dropbox confirmed a security breach on April 24th within its Dropbox Sign (formerly HelloSign) service, exposing customer data including email addresses, usernames, phone numbers, and hashed passwords. API keys, OAuth tokens, and authentication information... The post Dropbox Sign Data Breach: What You Need to Know and How to Protect Yourself appeared first on Penetration Testing.

WIRED Threat Level
MAY 1, 2024
Blockchain analysis firm Elliptic, MIT, and IBM have released a new AI model—and the 200-million-transaction dataset it's trained on—that aims to spot the “shape” of bitcoin money laundering.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Affairs
MAY 1, 2024
A new malware named Cuttlefish targets enterprise-grade and small office/home office (SOHO) routers to harvest public cloud authentication data. Researchers at Lumen’s Black Lotus Labs discovered a new malware family, named Cuttlefish, which targets enterprise-grade and small office/home office (SOHO) routers to harvest public cloud authentication data from internet traffic.

Penetration Testing
MAY 1, 2024
A significant security flaw has been discovered in the widely used XML-Crypto npm package, a tool integral to the cryptographic security of XML documents. This vulnerability, identified as CVE-2024-32962, carries the highest severity score... The post CVE-2024-32962 (CVSS 10): Critical Vulnerability in XML-Crypto Affects Millions appeared first on Penetration Testing.

Security Affairs
MAY 1, 2024
A former U.S. NSA employee has been sentenced to nearly 22 years in prison for attempting to sell classified documents to Russia. Jareh Sebastian Dalke (32), of Colorado Springs, is a former employee of the U.S. National Security Agency (NSA) who has been sentenced to nearly 22 years (262 months) in prison for attempting to transmit classified National Defense Information (NDI) to Russia.
Penetration Testing
MAY 1, 2024
go-secdump Package go-secdump is a tool built to remotely extract hashes from the SAM registry hive as well as LSA secrets and cached hashes from the SECURITY hive without any remote agent and without... The post go-secdump: remotely dump secrets from the Windows registry appeared first on Penetration Testing.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?
Let's personalize your content