BellaCPP: Discovering a new BellaCiao variant written in C++
SecureList
DECEMBER 20, 2024
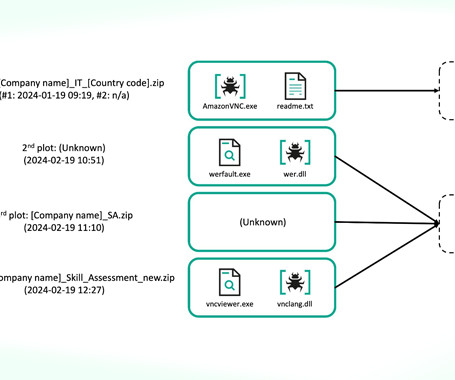
Introduction BellaCiao is a.NET-based malware family that adds a unique twist to an intrusion, combining the stealthy persistence of a webshell with the power to establish covert tunnels. It surfaced for the first time in late April 2023 and has since been publicly attributed to the APT actor Charming Kitten. One important aspect of the BellaCiao samples is how they exhibit a wealth of information through their respective PDB paths, including a versioning scheme we were able to work out once we








































Let's personalize your content