Security Analysis of the EU’s Digital Wallet
Schneier on Security
JUNE 27, 2024
A group of cryptographers have analyzed the eiDAS 2.0 regulation (electronic identification and trust services) that defines the new EU Digital Identity Wallet.

Schneier on Security
JUNE 27, 2024
A group of cryptographers have analyzed the eiDAS 2.0 regulation (electronic identification and trust services) that defines the new EU Digital Identity Wallet.

Tech Republic Security
JUNE 27, 2024
This guide covers various ransomware attacks, including Colonial Pipeline, WannaCry and LockBit, the systems hackers target and how to avoid becoming a victim and paying cybercriminals a ransom.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Hacker News
JUNE 27, 2024
TeamViewer on Thursday disclosed it detected an "irregularity" in its internal corporate IT environment on June 26, 2024. "We immediately activated our response team and procedures, started investigations together with a team of globally renowned cyber security experts and implemented necessary remediation measures," the company said in a statement.
Tech Republic Security
JUNE 27, 2024
Generative AI for enterprises can help or hurt. Here’s how to maintain trust in the age of AI.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
Bleeping Computer
JUNE 27, 2024
The remote access software company TeamViewer is warning that its corporate environment was breached in a cyberattack yesterday, with a cybersecurity firm claiming it was by an APT hacking group. [.

Trend Micro
JUNE 27, 2024
We analyze the multi-stage loading technique used by Water Sigbin to deliver the PureCrypter loader and XMRIG crypto miner.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
JUNE 27, 2024
Most organizations are uncertain about the effectiveness of their cybersecurity investments, despite increasing budgets and rampant cyber incidents, according to Optiv’s 2024 Threat and Risk Management Report. The post Security Budgets Grow, but Inefficiencies Persist appeared first on Security Boulevard.

The Hacker News
JUNE 27, 2024
A 22-year-old Russian national has been indicted in the U.S. for his alleged role in staging destructive cyber attacks against Ukraine and its allies in the days leading to Russia's full-blown military invasion of Ukraine in early 2022.

WIRED Threat Level
JUNE 27, 2024
AWS hosted a server linked to the Bezos family- and Nvidia-backed search startup that appears to have been used to scrape the sites of major outlets, prompting an inquiry into potential rules violations.

The Hacker News
JUNE 27, 2024
The peer-to-peer malware botnet known as P2PInfect has been found targeting misconfigured Redis servers with ransomware and cryptocurrency miners. The development marks the threat's transition from what appeared to be a dormant botnet with unclear motives to a financially motivated operation.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Malwarebytes
JUNE 27, 2024
On June 24, we observed a new campaign distributing a stealer targeting Mac users via malicious Google ads for the Arc browser. This is the second time in the past couple of months where we see Arc being used as a lure, certainly a sign of its popularity. It was previously used to drop a Windows RAT , also via Google ads. The macOS stealer being dropped in this latest campaign is actively being developed as an Atomic Stealer competitor, with a large part of its code base being the same as its pr

The Hacker News
JUNE 27, 2024
Did you know it’s now possible to build blockchain applications, known also as decentralized applications (or “dApps” for short) in native Python? Blockchain development has traditionally required learning specialized languages, creating a barrier for many developers… until now.

WIRED Threat Level
JUNE 27, 2024
Gutted of civil rights protections by Democrats to woo pro-business Republicans, the American Privacy Rights Act was pulled from a key congressional hearing—and appears unlikely to receive a full vote.

Security Affairs
JUNE 27, 2024
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds GeoSolutionsGroup JAI-EXT, Linux Kernel, and Roundcube Webmail bugs to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the following vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog : CVE-2022-24816 GeoSolutionsGroup JAI-EXT Code Injection Vulnerability CVE-2022-2586 Linux Kernel Use-After-Free Vulnerability CVE-2020-13965 Roundcube Webmail

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Hacker News
JUNE 27, 2024
While some SaaS threats are clear and visible, others are hidden in plain sight, both posing significant risks to your organization. Wing's research indicates that an astounding 99.7% of organizations utilize applications embedded with AI functionalities.
Security Affairs
JUNE 27, 2024
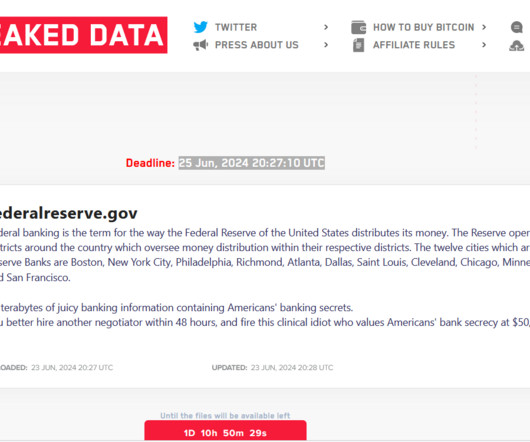
The LockBit ransomware group seems to have lied when they announced the hack of the US Federal Reserve. The real victim is the Evolve Bank. The LockBit ransomware group hasn’t hacked the Federal Reserve as it has recently claimed, the real victim is the Evolve Bank. Last week, the LockBit gang announced that it had breached the systems of the Federal Reserve of the United States and exfiltrated 33 TB of sensitive data, including “Americans’ banking secrets.

Trend Micro
JUNE 27, 2024
AI Pulse is a new blog series from Trend Micro on the latest cybersecurity AI news. In this edition: Siri says hi to OpenAI, fraud hogs the AI cybercrime spotlight, and why the Paris Olympics could be a hotbed of deepfakery.

Security Boulevard
JUNE 27, 2024
Researchers have identified three distinct nation-state campaigns leveraging advanced highly evasive and adaptive threat (HEAT) tactics. The post Three Nation-State Campaigns Targeting Healthcare, Banking Discovered appeared first on Security Boulevard.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

We Live Security
JUNE 27, 2024
A view of the H1 2024 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and research experts.

Bleeping Computer
JUNE 27, 2024
Microsoft pulled the June Windows 11 KB5039302 update after finding that it causes some devices to restart repeatedly. [.

The Last Watchdog
JUNE 27, 2024
Waltham, Mass., June 27, 2024, CyberNewsWire — Infinidat , a leading provider of enterprise storage solutions, has introduced a new automated cyber resiliency and recovery solution that will revolutionize how enterprises can minimize the impact of ransomware and malware attacks. Infinidat’s InfiniSafe® Automated Cyber Protection (ACP) is a first-of-its-kind cybersecurity integration solution that is designed to reduce the threat window of cyberattacks, such as ransomware.

Bleeping Computer
JUNE 27, 2024
Cloudflare, a lead provider of content delivery network (CDN) services, cloud security, and DDoS protection has warned that it has not authorized the use of its name or logo on the Polyfill.io website, which has recently been caught injecting malware on more than 100,000 websites in a significant supply chain attack. [.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
JUNE 27, 2024
Cloud security has become a major focus for organizations worldwide as they battle with a growing number of data breaches and application sprawl that makes defense more complicated. The post Cloud Security Tops Priority List for Organizations Globally appeared first on Security Boulevard.

Bleeping Computer
JUNE 27, 2024
A critical vulnerability is affecting certain versions of GitLab Community and Enterprise Edition products, which could be exploited to run pipelines as any user. [.
Veracode Security
JUNE 27, 2024
Here’s what you need to know about the progression of the Polyfill supply chain attack and how to respond. Overview of Polyfill Supply Chain Attack On June 25th, 2024, researchers at Sansec disclosed a supply chain attack affecting the polyfill.io content delivery network domain. This domain distributes the open-source polyfill.js library, which increases the compatible feature set of older browsers.

Google Security
JUNE 27, 2024
Posted by Chrome Root Program, Chrome Security Team The Chrome Security Team prioritizes the security and privacy of Chrome’s users, and we are unwilling to compromise on these values. The Chrome Root Program Policy states that CA certificates included in the Chrome Root Store must provide value to Chrome end users that exceeds the risk of their continued inclusion.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Bleeping Computer
JUNE 27, 2024
Geisinger, a prominent healthcare system in Pennsylvania, has announced a data breach involving a former employee of Nuance, an IT services provider contracted by the organization. [.

Webroot
JUNE 27, 2024
If you’re using cyber security software from Kaspersky Lab, Inc, you will need to find an alternative solution soon. On June 20, 2024, the U.S. Department of Commerce banned software from the Russian-owned company , saying it posed an unacceptable risk to national security. Citing the Russian government’s offensive cyber capabilities and its capacity to influence Kaspersky’s operations, Commerce Department regulators are strongly encouraging individuals and businesses that use Kaspersky products

SecureWorld News
JUNE 27, 2024
Luxury department store chain Neiman Marcus Group has become the latest victim in a series of cyberattacks targeting users of the Snowflake data warehousing platform. The breach affected nearly 65,000 shoppers and exposed sensitive personal information. In a letter to affected customers , Neiman Marcus stated: "We are writing to notify you of an issue that involves certain of your personal information.

Google Security
JUNE 27, 2024
Marios Pomonis, Software Engineer Google is committed to enhancing the security of open-source technologies, especially those that make up the foundation for many of our products, like Linux and KVM. To this end we are excited to announce the launch of kvmCTF, a vulnerability reward program (VRP) for the Kernel-based Virtual Machine (KVM) hypervisor first announced in October 2023.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content