How to make sure Adobe Flash is up-to-date and enabling it on-demand
We Live Security
OCTOBER 31, 2014
Learn how to update Adobe Flash Player, to help protect against malware attacks.
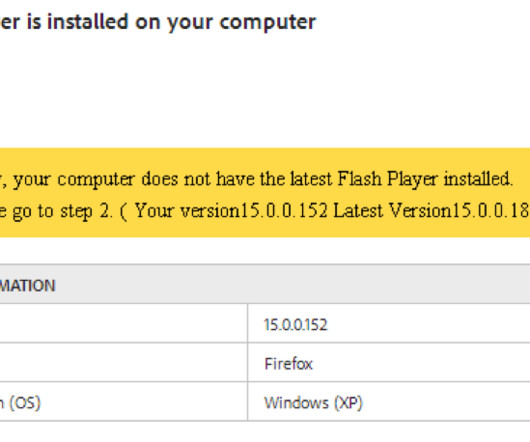
We Live Security
OCTOBER 31, 2014
Learn how to update Adobe Flash Player, to help protect against malware attacks.

NopSec
OCTOBER 16, 2014
Google security researchers Bodo Moller, Thai Duong and Krzysztof Kotowicz recently uncovered a vulnerability in SSL 3.0 that could allow secure connections to be compromised by attackers. The researchers are calling the attack POODLE, or Padding Oracle On Downgraded Legacy Encryption. “SSL 3.0 is nearly 18 years old, but support for it remains widespread,” Moller wrote in a blog post describing the issue. “Most importantly, nearly all browsers support it and, in order to
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Kali Linux
OCTOBER 5, 2014
Squash the Bugs with Kali 1.0.9a Over the past couple of weeks, we’ve seen a bunch of nasty bugs hit the scene, from shellshock to Debian apt vulnerabilities. As we prefer not to ship vulnerable ISOs, we’ve rolled up new images for our Kali Linux and NetHunter releases as well our Amazon AWS images with the relevant security fixes in place.
Spinone
OCTOBER 5, 2014
Spinbackup is a premier Cloud-to-Cloud Backup Cloud Cybersecurity solutions provider for G Suite and Office 365. The company is an authorized Google Partner featured on the G Suite Marketplace, and an Advanced Technology Partner of Amazon. Over 1,000 organizations with more than 150,000 G Suite users and 20,000 individual Google users currently rely on Spinbackup. […] The post Cloud Data Protection Investment for Spinbackup first appeared on SpinOne.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
We Live Security
OCTOBER 23, 2014
Last month, we presented The Evolution of Webinject in Seattle at the 24th Virus Bulletin conference. This blog post will go over its key findings and provide links to the various material that has been released in the last few weeks.

We Live Security
OCTOBER 22, 2014
Malware or malicious computer code has been around in some form or other for over 40 years, but the use of malware to take control of a group of computers that are then organized into something called a botnet is more a twenty-first century phenomenon.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
We Live Security
OCTOBER 15, 2014
Since October 2012, the European Cyber Security Month is going live as a pilot plan across Europe. Inspired by the concept of other similar projects that were successfully implemented around the globe. One of them is the Stop. Thinking. Connect campaign supported by the National Cyber Security Awareness Month in the United States.

We Live Security
OCTOBER 14, 2014
In this post we provide additional information on how a specially crafted PowerPoint slideshow file (.PPSX) led to the execution of a BlackEnergy dropper.
We Live Security
OCTOBER 9, 2014
For any security-conscious user, there are a few things worth remembering once you have secured that crucial invitation - we offer a few tips on how to get the most from the emoji-heavy network here.

NopSec
OCTOBER 3, 2014
If you are like us at NopSec one of the companies that operators on Amazon AWS cloud, this past couple of days resembled a lot more a perilous path. A series of reboot of the entire Amazon cloud forced us and most AWS-based cloud providers to spend long hours in the office or remotely to make sure things were in order after the reboot. “These updates must be completed by Oct. 1 before the issue is made public as part of an upcoming Xen Security Announcement (XSA),” according to the A

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

We Live Security
OCTOBER 31, 2014
Facebook has opened its doors to privacy concerned users, but opening up a dedicated Tor link, guaranteeing that people who visit the social networking site through anonymous browsers aren't mistaken for botnets, Gizmodo reports.

NopSec
OCTOBER 30, 2014
The term “security breach,” and other similar phrases, have become commonplace. This year alone we have seen the data of millions of people illicitly accessed and stolen from the networks of giants like Target, eBay, and JPMorgan Chase. Each week there seems to be a new report on some company falling prey to ever-ready attackers. In order to continue successful business operations, maintain customer trust, and build a strong brand reputation, everyone from the CEO to the network analyst needs to

We Live Security
OCTOBER 23, 2014
An army of the undead, wreaking havoc on the Internet it's a nightmare scenario that has played out many times as the population of humans online has exploded. Some zombie plagues have been particularly troubling, and we will take a look at the worst of the worst.

We Live Security
OCTOBER 21, 2014
In this post we want to share with you a question that arose from the first post in this series: whether exploits are the same as malware. What are we talking about? The best way to debunk any myth is to start by understanding what it is we are talking about.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

We Live Security
OCTOBER 20, 2014
As promised in our post about the European Cyber Security Month during October, we are publishing about Botnets and Exploits this week. Even though we had the Poodle flaw in the web encryption standard a few days ago, we are using this week to explain what are botnets and exploits and how they work.

We Live Security
OCTOBER 16, 2014
Facebook is introducing a new feature targeted at users it believes are in or near a disaster zone to let their loved ones know they are okay, according to The Independent.

NopSec
OCTOBER 10, 2014
It is no secret that hackers have been making the rounds, targeting organizations of all sizes, from national retailers to local financial institutions, using familiar exploits like Heartbleed and Shellshock to execute their hits. This recent spate of malicious attacks has shown just how vulnerable our Internet-based world is. In the era of ‘Internet of Things’, minor flaws can have catastrophic consequences if vulnerabilities are not fixed in time.

NopSec
OCTOBER 10, 2014
Call it good timing. After all the horrendous cybersecurity news of the past weeks, it feels great about that our industry is joining forces, strengthening partnership alliance within the infosec community, and collaborating at Qualys’ annual security conference in Las Vegas this week. Speaking for myself (and perhaps the rest of the NopSec team), I’m especially energized to surround myself with the best and brightest minds in the security when dealing with one of the worst weeks in vulnerabilit

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
Let's personalize your content