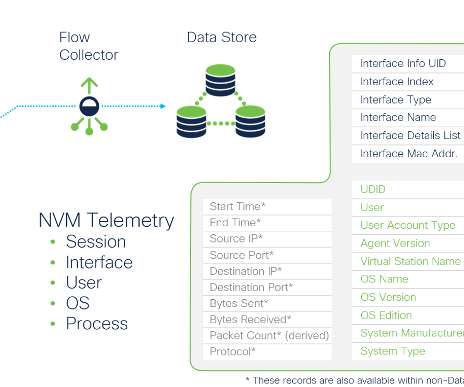
Complete and continuous remote worker visibility with Network Visibility Module data as a primary telemetry source
Cisco Security
JUNE 22, 2021
Organizations are currently facing new challenges related to monitoring and securing their remote workforces. Many users don’t always use their VPNs while working remotely – this creates gaps in visibility that increase organizational risks. It just comes with the territory. Plain and simple.
















Let's personalize your content