HTML Smuggling technique used in phishing and malspam campaigns
Security Affairs
NOVEMBER 12, 2021
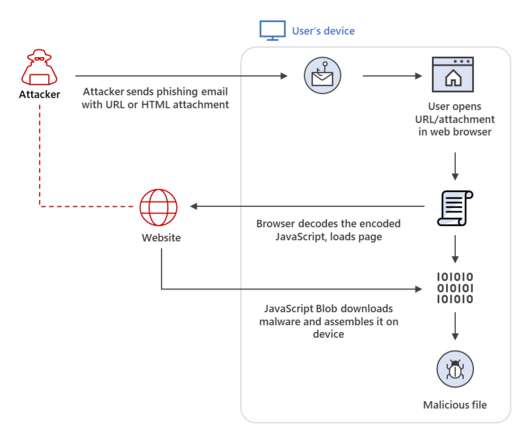
— Microsoft Security Intelligence (@MsftSecIntel) July 23, 2021. “Thus, instead of having a malicious executable pass directly through a network, the attacker builds the malware locally behind a firewall.” The malicious payloads are delivered via encoded strings in an HTML attachment or webpage. .”













Let's personalize your content