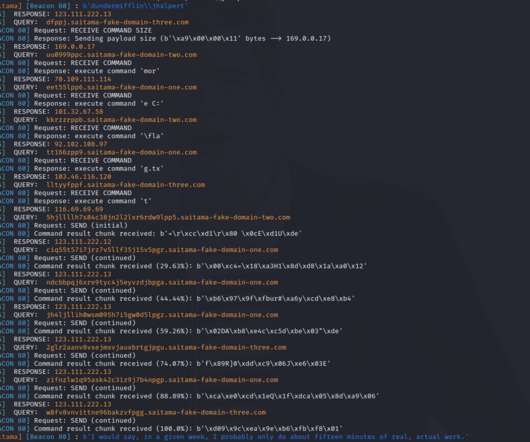
Introduction of DNS tunneling and how attackers use it.
Quick Heal Antivirus
APRIL 26, 2022
What is DNS? DNS (Domain Name System) is a service that converts hostnames to IP addresses. The post Introduction of DNS tunneling and how attackers use it. appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.












Let's personalize your content