New Linux Malware Shikitega Can Take Full Control of Devices
eSecurity Planet
SEPTEMBER 15, 2022
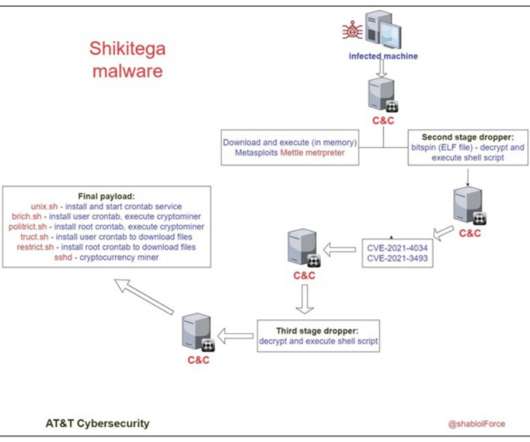
AT&T Alien Labs has discovered a new Linux malware that can be used for highly evasive attacks, as the infection has been designed for persistence and runs on practically all kinds of Linux devices. Researchers dubbed the malware “Shikitega.” Two of them regard the current user and the rest are for the root account.










Let's personalize your content