New Linux Malware Shikitega Can Take Full Control of Devices
eSecurity Planet
SEPTEMBER 15, 2022
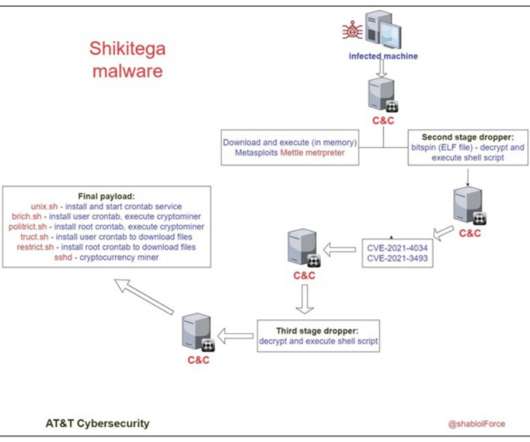
This strategy seems to be a trade-off, as such services are way easier to take down by authorities, but it allows bypassing network security products that don’t block legitimate providers. AT&T labs provided a list of IoCs (indicators of compromise) that system administrators can use to add specific rules to security solutions.











Let's personalize your content