GTPDOOR: The Shape-Shifting Threat Lurking in Telco Networks
Penetration Testing
FEBRUARY 29, 2024
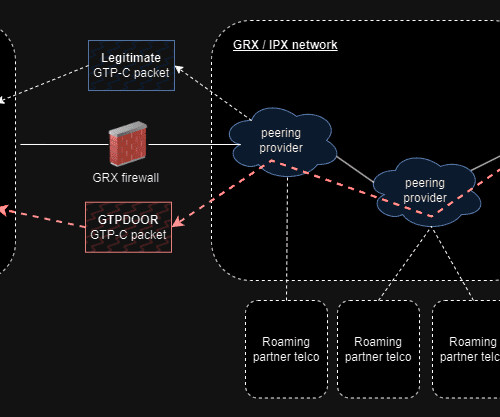
A new Linux-based malware, christened GTPDOOR, has emerged with a cunning strategy to infiltrate the heart of telecommunication networks – the GRX (GPRS Roaming Exchange).
















Let's personalize your content