Here is why you should have Cobalt Strike detection in place
CSO Magazine
NOVEMBER 28, 2022
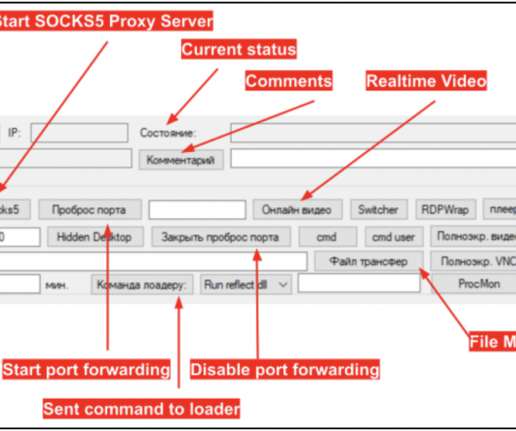
Google recently released a list of YARA detection rules for malicious variants of the legitimate Cobalt Strike penetration testing framework that are being used by hackers in the wild. Living off the land is a common tactic.














Let's personalize your content