Threat actors actively exploit Control Web Panel RCE following PoC release
Security Affairs
JANUARY 12, 2023
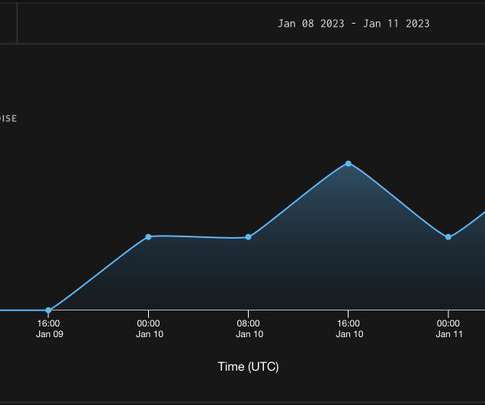
CENTOS Web Panel RCE CVE-2022-44877 Attempt Tag is live and we're definitely seeing activity [link] pic.twitter.com/CXo8WSSRag — GreyNoise (@GreyNoiseIO) January 11, 2023. SecurityAffairs – hacking, Moshen Dragon). The vulnerability was discovered by Numan Türle from Gais Security. Pierluigi Paganini.











Let's personalize your content