Israel’s Naftali Bennett Becomes The First Head of Government To Emerge From The CyberSecurity Industry
Joseph Steinberg
JUNE 14, 2021
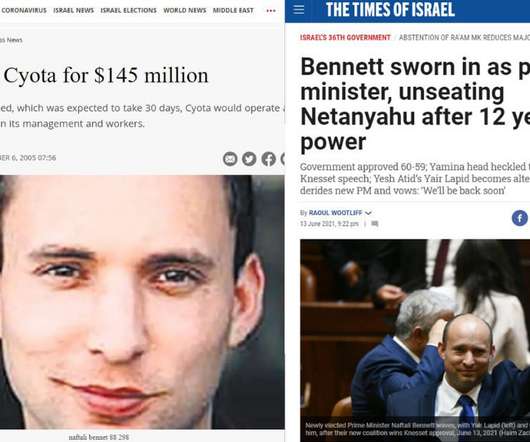
Bennett spent several years as the New York-based CEO of the firm, before he and his partners sold Cyota to RSA Security in 2005 for $145 Million. Bennett, who is also the first Prime Minister to emerge from Israel’s high-tech industry, co-founded what would eventually become the cybersecurity firm, Cyota , in 1999.
















Let's personalize your content