U.S. Hacks QakBot, Quietly Removes Botnet Infections
Krebs on Security
AUGUST 29, 2023
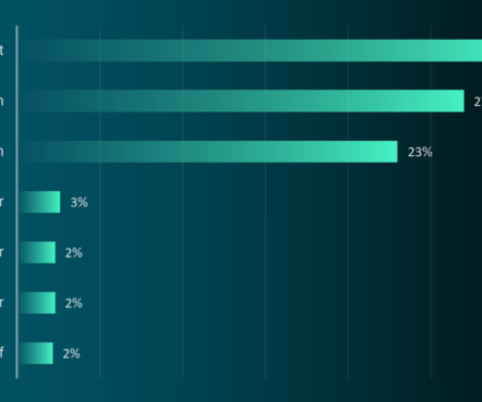
Emerging in 2007 as a banking trojan, QakBot (a.k.a. According to recent figures from the managed security firm Reliaquest , QakBot is by far the most prevalent malware “loader” — malicious software used to secure access to a hacked network and help drop additional malware payloads.











Let's personalize your content