Naikon APT group uses new Nebulae backdoor in attacks aimed at military orgs
Security Affairs
APRIL 28, 2021
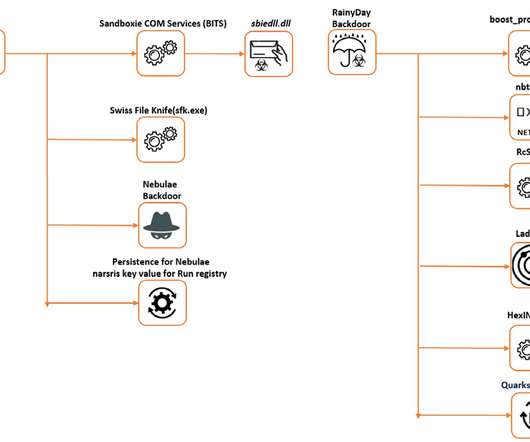
The Naikon APT group is a China-linked cyber espionage group that has been active at least since 2010 and that remained under the radar since 2015 while targeting entities in Asia-Pacific (APAC) region. . “The malicious activity was conducted between June 2019 and March 2021. .












Let's personalize your content