MY TAKE: Memory hacking arises as a go-to tactic to carry out deep, persistent incursions
The Last Watchdog
MARCH 4, 2019
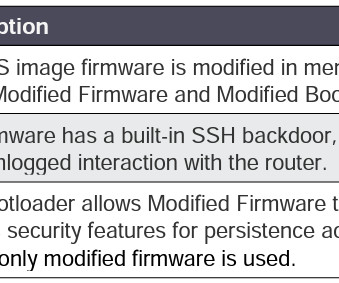
Related: We’re in the midst of ‘cyber Pearl Harbor’ Peel back the layers of just about any sophisticated, multi-staged network breach and you’ll invariably find memory hacking at the core. Virsec is a leading innovator of memory protection technologies. Here’s what I took away from our discussion: Transient hacks.










Let's personalize your content