A Basic Timeline of the Exchange Mass-Hack
Krebs on Security
MARCH 8, 2021
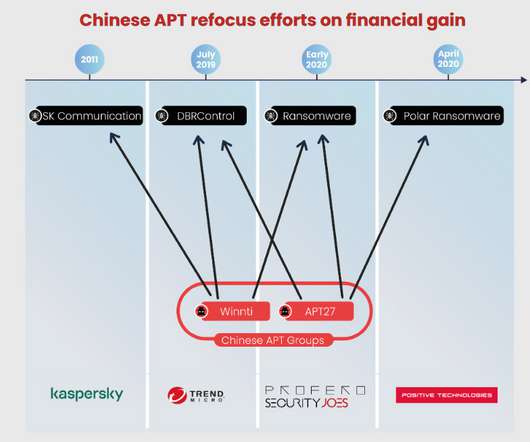
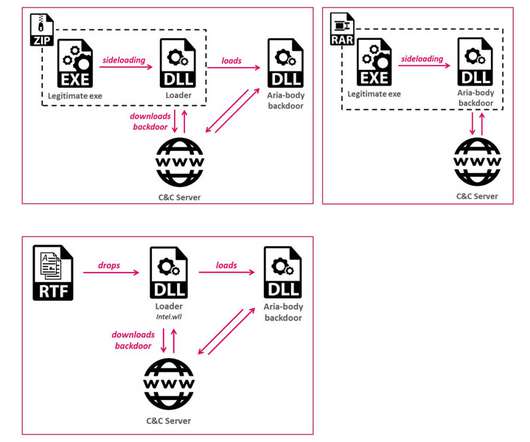
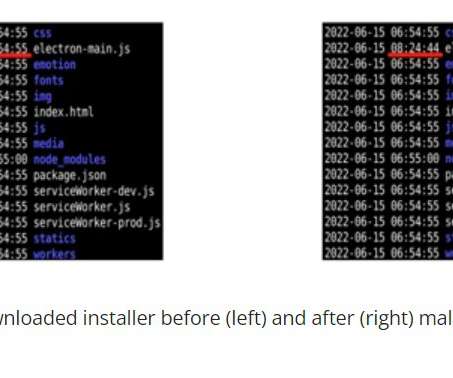
Here’s a brief timeline of what we know leading up to last week’s mass-hack, when hundreds of thousands of Microsoft Exchange Server systems got compromised and seeded with a powerful backdoor Trojan horse program. When did Microsoft find out about attacks on previously unknown vulnerabilities in Exchange? .









































Let's personalize your content