Russian govn blocked Tutanota service in Russia to stop encrypted communication
Security Affairs
FEBRUARY 17, 2020
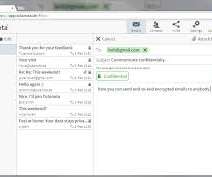
Tutanota , the popular free and open-source end-to-end encrypted email software, has been blocked by Russian authorities. The popular free and open-source end-to-end encrypted email service Tutanota has been blocked in Russia on Friday evening. ” states Tutanota. reported the Associated Press. . Pierluigi Paganini.




















Let's personalize your content