US pharmacy Rite Aid banned from operating facial recognition systems
Malwarebytes
DECEMBER 21, 2023
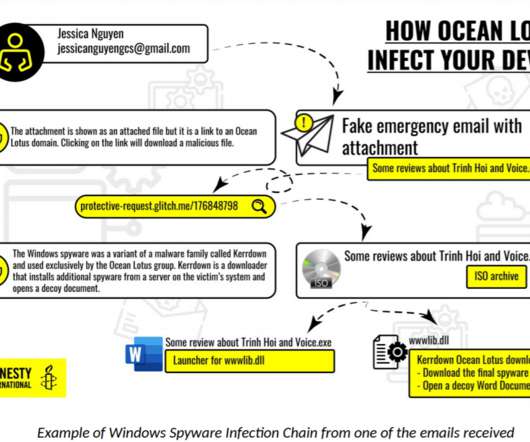
The regulator found so many flaws in the retailer’s surveillance program that it concluded Rite Aid had failed to implement reasonable procedures and prevent harm to consumers in its use of facial recognition technology in hundreds of stores. It failed to monitor or test the accuracy of the technology after deployment.










Let's personalize your content