How to Stop Ransomware: Breach Prevention vs. Cobalt Strike Backdoor
Security Boulevard
JANUARY 12, 2022
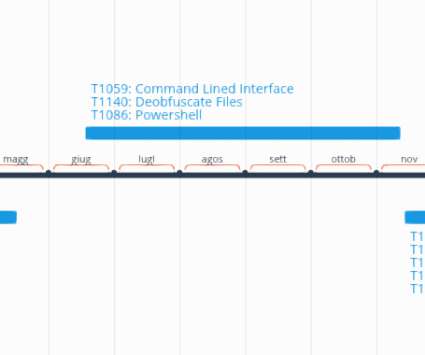
With a year-on-year increase of over 161% , malicious usage of cracked versions of Cobalt Strike (a legitimate penetration test tool) is skyrocketing. Developed in 2012 to give pen testers and red teams the capability to conduct hard-to-spot test attacks, Cobalt Strike is designed to be dynamic and evasive.
















Let's personalize your content