Microsoft’s case study: Emotet took down an entire network in just 8 days
Security Affairs
APRIL 4, 2020
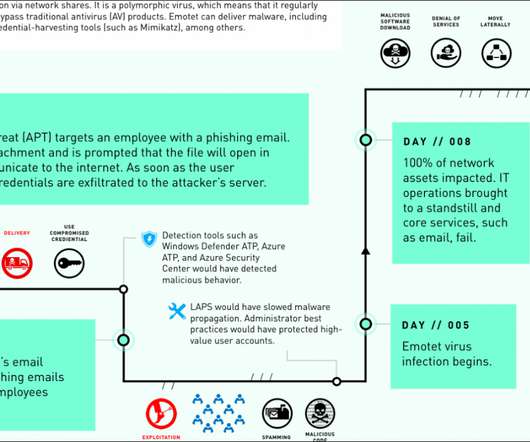
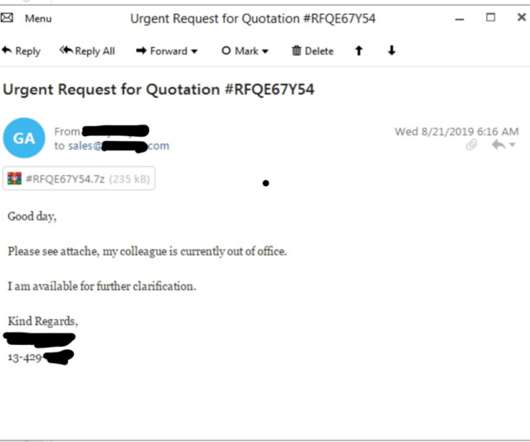
Microsoft declared that an Emotet attack took down an organization’s network by overheating all the computers and bringing its Internet access down. “He’d been told the organization had an extensive system to prevent cyberattacks, but this new virus evaded all their firewalls and antivirus software. .




















Let's personalize your content