InfectedSlurs botnet targets QNAP VioStor NVR vulnerability
Security Affairs
DECEMBER 17, 2023
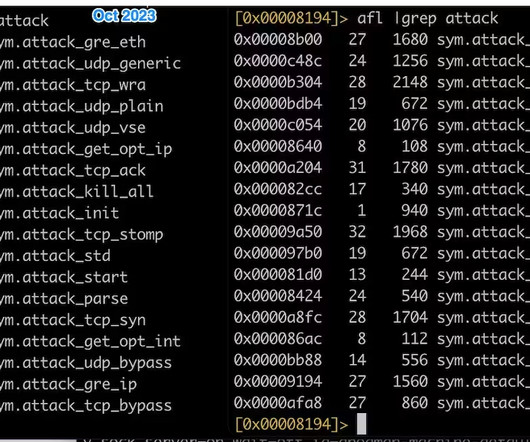
On December 6, The Akamai Security Intelligence Response Team (SIRT) published the first update to the InfectedSlurs advisory series. The security firm revealed that threat actors were exploiting a vulnerability, tracked as CVE-2023-49897 (CVSS score 8.0) released June 21, 2014). and earlier. and earlier (5.0.0












Let's personalize your content