Microsoft releases open-source tool for checking MikroTik Routers compromise
Security Affairs
MARCH 17, 2022
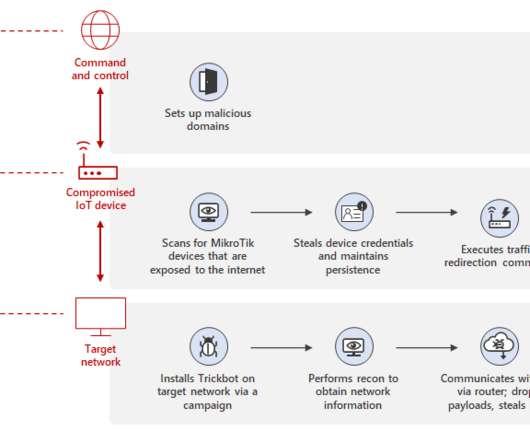
We published this tool to help customers ensure these IoT devices are not susceptible to these attacks.” The news wave of attacks aimed at cryptocurrency firms, most of them located in the U.S. The news wave of attacks aimed at cryptocurrency firms, most of them located in the U.S. Pierluigi Paganini.











Let's personalize your content