Operation Falcon: Group-IB helps INTERPOL identify Nigerian BEC ring members
Security Affairs
NOVEMBER 25, 2020
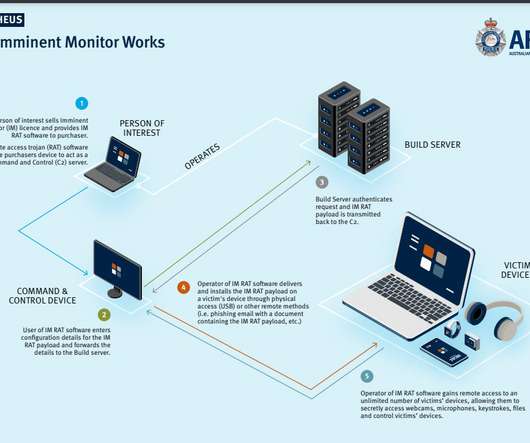
Group-IB supported an INTERPOL-led operation Falcon targeting business email compromise cybercrime gang from Nigeria, dubbed TMT. Group-IB , a global threat hunting and intelligence company, supported an INTERPOL-led operation Falcon targeting business email compromise (BEC) cybercrime gang from Nigeria, dubbed TMT by Group-IB.














Let's personalize your content