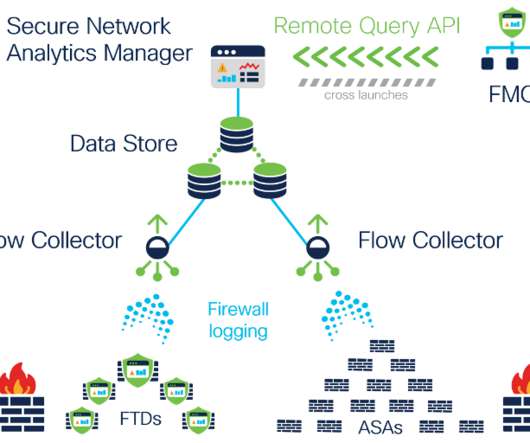
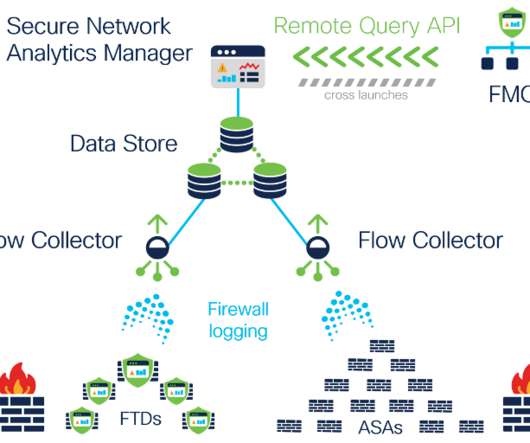
Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
Cisco Security
JUNE 1, 2021
To briefly level-set, let’s take a quick step back in time – way back to 2019 before the “work from home (WFH) era” had begun to illustrate the gravity of the paradigm shift that occurred over the past two years and its security implications. To summarize, visibility evaporated, and meanwhile, organizational risk levels spiked parabolically.












Let's personalize your content