March Madness and Distracted Employees – Bracket Busted
Thales Cloud Protection & Licensing
MARCH 27, 2019
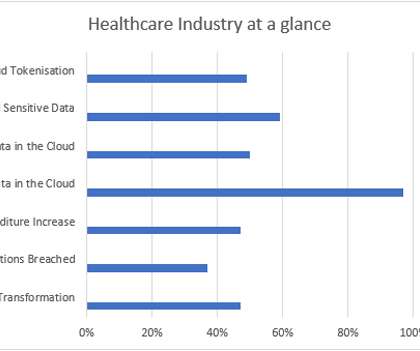
Employees are the first line of defense when it comes to averting phishing attempts and distracted employees are off their game. Our 2019 Data Threat Report-Global Edition , revealed that 97% of survey respondents reported their organization was already underway with some level of digital transformation.















Let's personalize your content