How Secure Shell (SSH) Keys Work
Security Boulevard
AUGUST 5, 2022
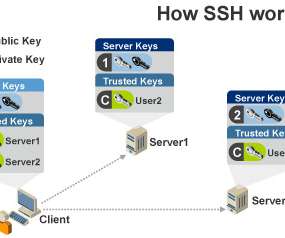
It was originally published on February 5, 2019. ) . All enterprises rely on Secure Shell (SSH) keys to authenticate privileged users and establish trusted access to critical systems, including application servers, routers, firewalls, virtual machines, cloud instances, and many other devices and systems. Related blogs.













Let's personalize your content