Why access management needs to evolve beyond passwords
CyberSecurity Insiders
OCTOBER 13, 2021
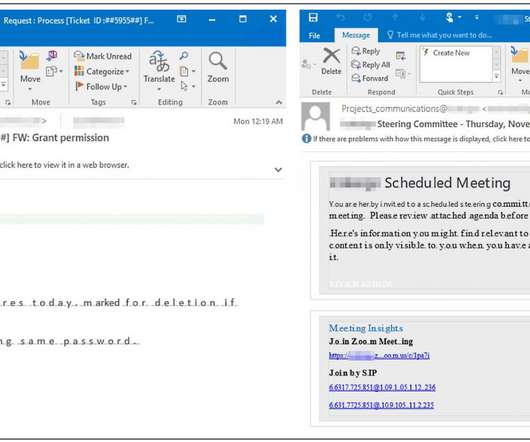
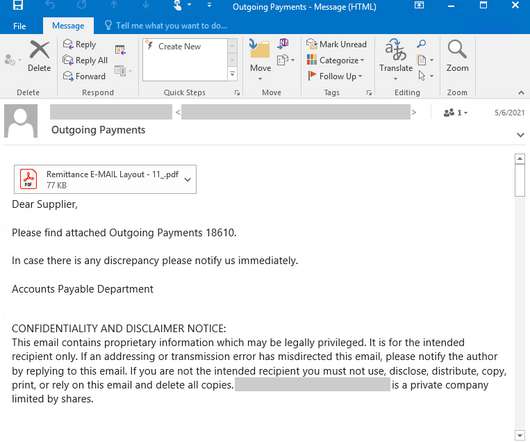
Problems arise for businesses when they base their access management programs entirely around passwords, however. Such programs overlook the burden that passwords can cause to users as well as to IT and security teams. Passwords: An unsustainable business cost. Users have too many passwords to remember on their own.














Let's personalize your content