ESET Threat Report H1 2025
We Live Security
JUNE 26, 2025
The H1 2025 issue of the ESET Threat Report reviews the key trends and developments that shaped the threat landscape from November 2024 to May 2025
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

We Live Security
JUNE 26, 2025
The H1 2025 issue of the ESET Threat Report reviews the key trends and developments that shaped the threat landscape from November 2024 to May 2025

eSecurity Planet
MARCH 3, 2025
In a comprehensive new report, cybersecurity leader CrowdStrike unveiled a rapidly evolving threat landscape that challenges traditional defenses. Unprecedented speed and scale of attacks The report reveals that some cyberattacks break out within 51 seconds, with an average breach time of 48 minutes.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Thales Cloud Protection & Licensing
MAY 27, 2025
AI, Quantum and the Evolving Threat Landscape: Key Findings from the Thales 2025 Data Threat Report madhav Tue, 05/27/2025 - 07:40 The Thales 2025 Data Threat Report reveals a critical inflection point in global cybersecurity. Encouragingly, businesses are taking steps in the right direction.

Thales Cloud Protection & Licensing
MAY 26, 2025
AI, Quantum and the Evolving Threat Landscape: Key Findings from the Thales 2025 Data Threat Report madhav Tue, 05/27/2025 - 04:40 The Thales 2025 Data Threat Report reveals a critical inflection point in global cybersecurity. Encouragingly, businesses are taking steps in the right direction.

We Live Security
JULY 1, 2025
ESET Chief Security Evangelist Tony Anscombe reviews some of the report's standout findings and their implications for organizations in 2025 and beyond

Penetration Testing
JUNE 1, 2025
Meta's Q1 2025 report details the takedown of covert influence campaigns from China, Iran, and Romania, utilizing AI and fake accounts to manipulate public discourse.

The Hacker News
MAY 29, 2025
Meta on Thursday revealed that it disrupted three covert influence operations originating from Iran, China, and Romania during the first quarter of 2025. "We We detected and removed these campaigns before they were able to build authentic audiences on our apps," the social media giant said in its quarterly Adversarial Threat Report.

eSecurity Planet
MAY 1, 2025
The RSA Conference 2025, held in San Francisco from April 28 to May 1, spotlighted the evolving landscape of cybersecurity, with a strong emphasis on artificial intelligence, identity security, and collaborative defense strategies. This years theme (Many Voices. Protection against deepfakes, fraud, outages, and AI-based impersonation.

Security Affairs
JUNE 22, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Critical Langflow Vulnerability (CVE-2025-3248) Actively Exploited to Deliver Flodrix Botnet Predator Still Active, with New Client and Corporate Links Identified Threat Group Targets Companies in Taiwan Feeling Blue(Noroff): (..)

SecureWorld News
JUNE 6, 2025
The Honeywell 2025 Cyber Threat Report delivers a sobering snapshot of today's industrial cybersecurity landscape: cyberattacks targeting operational technology (OT) environments are no longer rare or speculative—they're persistent, highly targeted, and increasingly sophisticated. Register for free here.

Security Boulevard
FEBRUARY 19, 2025
Cybercrime-as-a-Service (CaaS) now accounts for 57% of all cyberthreats, marking a 17% increase from the first half of 2024, according to Darktraces Annual Threat Report. The post CaaS Surges in 2025, Along With RATs, Ransomware appeared first on Security Boulevard.

Thales Cloud Protection & Licensing
JULY 23, 2025
Passwordless 360°: The Evolution of Authentication in 2025 madhav Thu, 07/24/2025 - 06:13 Although passwords have been one of the foundations of digital security for many years, they are one of the weakest links in the enterprise's cybersecurity chain. As relics, it’s high time we got rid of them.

Thales Cloud Protection & Licensing
FEBRUARY 3, 2025
What 2025 HIPAA Changes Mean to You madhav Tue, 02/04/2025 - 04:49 Thales comprehensive Data Security Platform helps you be compliant with 2025 HIPAA changes. You expect Personal Health Information (PHI) to be protected, thankfully due to HIPAA Compliance. HIPAA is not a static regulation. What Changed?

We Live Security
JULY 22, 2025
Editor 22 Jul 2025 Your digital footprint is more valuable than you think. Learn why your digital footprint is so valuable, and when you might actually be the product. Its not just a trail of data left behind by your online activity – its a goldmine of sensitive data.

Thales Cloud Protection & Licensing
OCTOBER 24, 2024
Several key provisions of the amended regulations will take effect on November 1, 2024, with additional measures rolling out in 2025. Some of the key findings from the report include: The percentage of financial services organizations reporting a breach in the last 12 months decreased from 29% in 2021 to 14% in 2024.
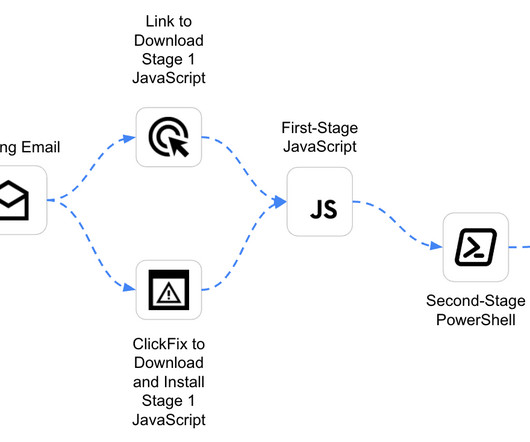
Security Affairs
MAY 5, 2025
MintsLoader is used by several threat groups, notably TAG-124. In early 2025, Recorded Future researchers observed a phishing campaign targeting the U.S. If the system fails validation, the C2 may deliver a decoy executable like AsyncRAT, which has led to misclassifications in threat reports.

Thales Cloud Protection & Licensing
MAY 7, 2025
Phishing-Resistant MFA: Why FIDO is Essential madhav Thu, 05/08/2025 - 04:47 Phishing attacks are one of the most pervasive and insidious threats, with businesses facing increasingly sophisticated and convincing attacks that exploit human error.

Security Affairs
JUNE 22, 2025
CISA adds Apple products, and TP-Link routers flaws to its Known Exploited Vulnerabilities catalog Attackers target Zyxel RCE vulnerability CVE-2023-28771 India-based car-sharing company Zoomcar suffered a data breach impacting 8.4M

Hacker's King
DECEMBER 21, 2024
YOU MAY ALSO WANT TO READ ABOUT: WhatsApps New Year 2025 Update: Grab These 3 Festive Features Before Theyre Gone The Role of Generative AI in Cybersecurity Generative AI refers to artificial intelligence systems capable of creating content, such as images, text, and code, by learning patterns from data.

Security Affairs
JUNE 29, 2025
House banned WhatsApp on government devices due to security concerns Russia-linked APT28 use Signal chats to target Ukraine official with malware China-linked APT Salt Typhoon targets Canadian Telecom companies U.S.

Thales Cloud Protection & Licensing
MAY 19, 2025
Your Data, Your Responsibility: Securing Your Organization's Future in the Cloud madhav Tue, 05/20/2025 - 04:37 Cloud adoption has fundamentally changed the way businesses operate, offering scalability, agility, and cost efficiencies that were unimaginable just a decade ago.

Security Boulevard
MAY 19, 2025
Your Data, Your Responsibility: Securing Your Organization's Future in the Cloud madhav Tue, 05/20/2025 - 04:37 Cloud adoption has fundamentally changed the way businesses operate, offering scalability, agility, and cost efficiencies that were unimaginable just a decade ago.

Thales Cloud Protection & Licensing
JULY 10, 2025
Thales AI Cybersecurity: Using AI, Protecting AI, Protecting Against AI madhav Thu, 07/10/2025 - 11:53 The growing threat of AI to cybersecurity and technology resources proved the prevailing topic at RSA this year, alongside the desire to harness its power positively and productively.

Penetration Testing
JULY 9, 2025
A recent update embeds a persistent backdoor, turning what was once a hit-and-run data thief into a long-term intruder capable of remote command execution, system surveillance, and re-infection. If this article helped you, please share it with others who might benefit.

We Live Security
JULY 4, 2025
Phil Muncaster 04 Jul 2025 • , 4 min. Here’s how to avoid getting played by gamified job scams. read Many of us have been experiencing a cost-of-living crisis for years, and the news headlines remain filled with doom-laden predictions of what the future might hold.

Thales Cloud Protection & Licensing
JULY 1, 2025
Cloud Encryption: What Your Cloud Provider Covers -- and What’s Still on You madhav Wed, 07/02/2025 - 05:58 The Thales 2025 Data Threat Report revealed that cloud assets such as SaaS applications, cloud-based storage, and cloud infrastructure management were the greatest targets for attack.

Security Boulevard
MARCH 3, 2025
This is a news item roundup of privacy or privacy-related news items for 23 FEB 2025 - 1 MAR 2025. The post Privacy Roundup: Week 9 of Year 2025 appeared first on Security Boulevard. Information and summaries provided here are as-is for warranty purposes. The manufacturer (Hirsch) does not plan a security fix.

SecureWorld News
DECEMBER 27, 2024
While the latter is more of a good thing, all of these are realities and none of the three will go away in 2025. We curated some predictions for the cybersecurity industry in 2025--some specific; some broad; some from practitioners; some from vendors--to get a pulse on what the cybersecurity community believes is coming in the New Year.

Thales Cloud Protection & Licensing
JUNE 10, 2025
Why Data Sovereignty and Privacy Matter to You—Not Just Nations madhav Tue, 06/10/2025 - 10:17 It started with a well-meaning mistake. Bernie, a project manager at a mid-Atlantic regional health provider, was coordinating a data science initiative with an external partner. The company was paralyzed.

Thales Cloud Protection & Licensing
FEBRUARY 17, 2025
Centralised, Scalable, Compliant: Keeping Your Data Safer with Enterprise Key Management madhav Tue, 02/18/2025 - 04:50 The rise of multi-cloud environments, hybrid infrastructures, and stricter regulatory requirements has made cryptographic key management a major priority for enterprises around the world.

Trend Micro
JUNE 26, 2025
By: Trend Micro June 27, 2025 Read time: ( words) Save to Folio Organizations invest in advanced tools to secure their assets, but humans are still the most persistent attack vector. Each year, this is reinforced by the overwhelming number of breaches that stem from human behaviour. All rights reserved.

Security Affairs
MAY 30, 2025
The Adversarial Threat Report published by the company also includes Threat indicators for the ablot campaigns. ” reads the Metas Adversarial Threat Report, First Quarter 2025. ” reads the Metas Adversarial Threat Report, First Quarter 2025.

Security Boulevard
JUNE 7, 2025
According to CrowdStrike’s recent Threat Report, over 80% of today’s attacks bypass traditional signature-based systems, exploiting the gaps in rules and static detections. Novel attacks, including zero-days and advanced persistent threats (APTs), have soared. Customers are vulnerable, and they know it.

Trend Micro
JUNE 10, 2025
By: Eduardo Golcman, Stefano Olivieri, Fernando Cardoso, Felipe Costa June 11, 2025 Read time: ( words) Save to Folio Introduction Containers have transformed the way we develop, deploy, and manage software. All rights reserved. sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

Thales Cloud Protection & Licensing
APRIL 7, 2025
Identity at a Crossroads: Why Existential Identity Matters madhav Tue, 04/08/2025 - 04:31 Imagine waking up one morning to find your digital identity compromised your accounts hijacked, your access revoked, and your data in someone elses hands. Are We Sacrificing Safety for Simplicity?

Trend Micro
JUNE 10, 2025
By: Marianne Lee June 11, 2025 Read time: ( words) Save to Folio On a rainy, grey afternoon in a UK film studio, I sat down with Managing Director at NEOM McLaren Electric Racing, Ian James, VP Cybersecurity at Trend Micro, Greg Young, and our host, Finola Roycroft. All rights reserved. sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

Thales Cloud Protection & Licensing
JULY 21, 2025
AI Can’t Be Trusted—But It Still Needs Your Trust madhav Tue, 07/22/2025 - 05:21 It’s impossible to ignore the seismic impact of Generative AI (GenAI) on enterprise operations. We’re talking about business threats to integrity, trust, and reputation. By 2025, that’s improved, but only to 24%. It doesn’t just generate output.

Thales Cloud Protection & Licensing
MAY 7, 2025
Thales Named an Overall Leader in 2025 KuppingerCole Leadership Compass for Enterprise Secrets Management madhav Thu, 05/08/2025 - 06:31 Were proud to share that Thales has been recognized as an Overall Leader in the 2025 KuppingerCole Leadership Compass for Enterprise Secrets Management.

Trend Micro
JULY 2, 2025
It offers previously out-of-reach opportunities for business leaders to anticipate market trends and make better decisions. All rights reserved. sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

Security Affairs
JULY 20, 2025
Fortinet FortiWeb flaw CVE-2025-25257 exploited hours after PoC release Authorities released free decryptor for Phobos and 8base ransomware Anne Arundel Dermatology data breach impacts 1.9 Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Tbps assault U.S.

Security Boulevard
MAY 26, 2025
AI, Quantum and the Evolving Threat Landscape: Key Findings from the Thales 2025 Data Threat Report madhav Tue, 05/27/2025 - 04:40 The Thales 2025 Data Threat Report reveals a critical inflection point in global cybersecurity. Encouragingly, businesses are taking steps in the right direction.

Digital Shadows
FEBRUARY 24, 2025
Editors note: This report was authored by Kimberley Bromley, Hayden Evans, and Joseph Keyes. Today, were proud to present the ReliaQuest Annual Cyber-Threat Report: 2025. Now in its third year, this report offers a close look at the top cyber threats our customers faced throughout 2024.

Tech Republic Security
FEBRUARY 26, 2025
SonicWalls 2025 Annual Threat Report noted the U.S. healthcare sector and Latin America were targeted by cybercriminals.

We Live Security
DECEMBER 16, 2024
ESET Chief Security Evangelist Tony Anscombe looks at some of the report's standout findings and their implications for staying secure in 2025
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content