North Korea-linked APT37 exploited IE zero-day in a recent attack
Security Affairs
OCTOBER 19, 2024
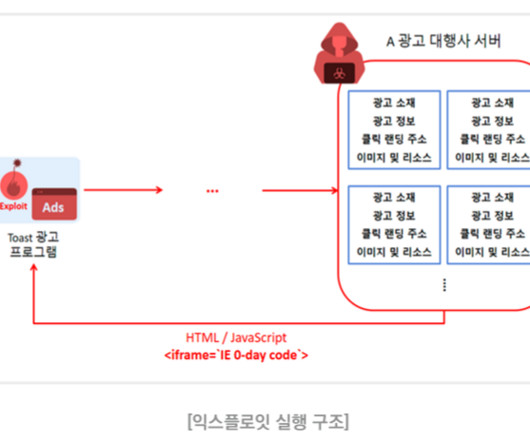
The vulnerability is a scripting engine memory corruption issue that could lead to arbitrary code execution. As a result, TA-RedAnt exploited the toast ad program that were using the vulnerable IE browser engine (jscript9.dll), ” reads the advisory published by Microsoft, which addressed the flaw in August.











Let's personalize your content