How 5G Operators Can Prepare for The Quantum Era
Thales Cloud Protection & Licensing
JANUARY 29, 2024
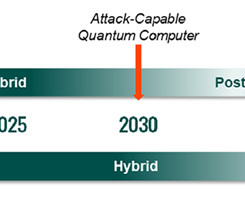
This expansion and significant architectural changes will create highly complex networks, exposing new vulnerabilities and more significant risks as we move towards a post-quantum (PQ) world. Hybrid cryptography can secure data in motion by combining symmetric encryption with public key ciphers. Find Thales in Hall 2, Stand 2J30.









Let's personalize your content