Network Security 101 – Definition, Types, Threats, and More
Heimadal Security
MARCH 17, 2022
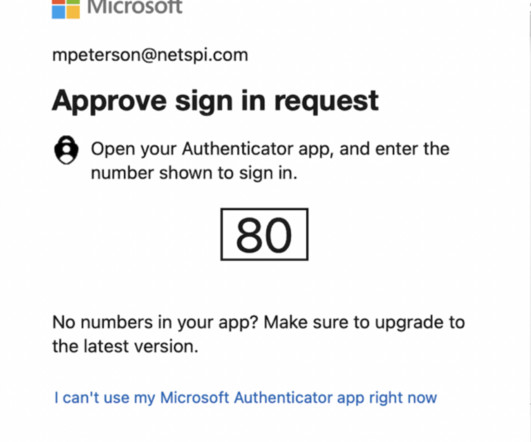
As society evolves more and more towards the dynamic workplace, the modern enterprise is faced with increased network security risks. In this article, you will find the definition of network security, […]. How can you defend your company’s assets and perimeter, both online and offline?






















Let's personalize your content