Top Unexpected Ways to Utilise a Password Manager for Enhanced Security and Organisation
IT Security Guru
JANUARY 22, 2024
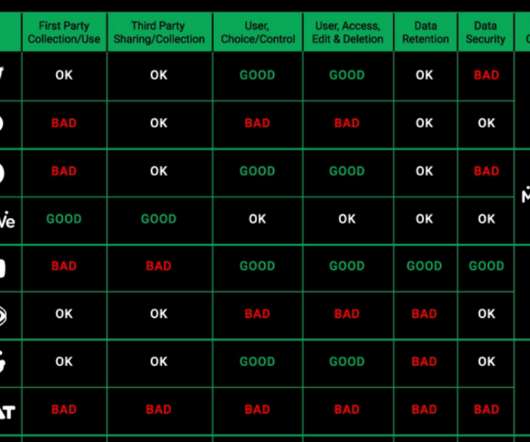
Users can save credit card details that can be easily filled on retail websites, as well as bank information such as account and routing numbers. This information can be securely shared with others with full end-to-end encryption, ensuring your most sensitive financial information is never exposed via unsecure channels.













Let's personalize your content