Zloader, another botnet, bites the dust
Malwarebytes
APRIL 14, 2022
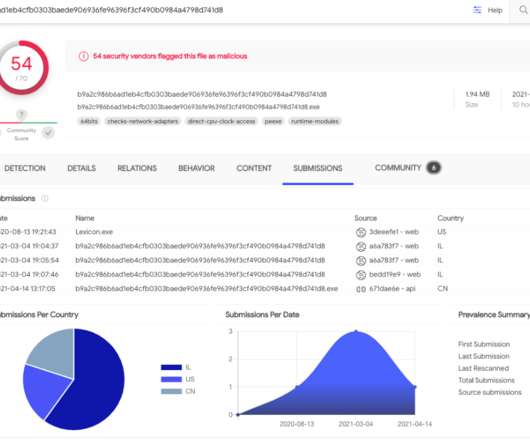
The primary goal of Zloader was originally financial theft, stealing account login IDs, passwords and other information to take money from people’s accounts. But Zloader also includes a component that disables popular security and antivirus software, thereby preventing victims from detecting the Zloader infection on their systems.
















Let's personalize your content