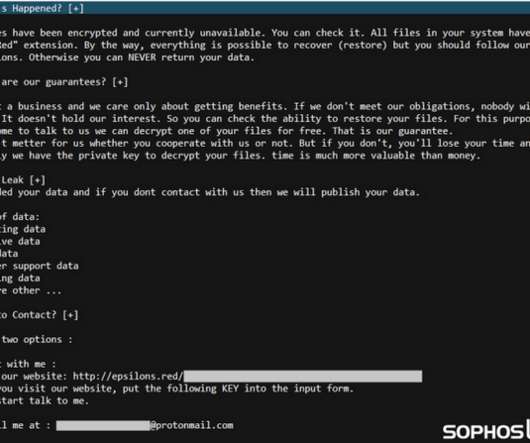
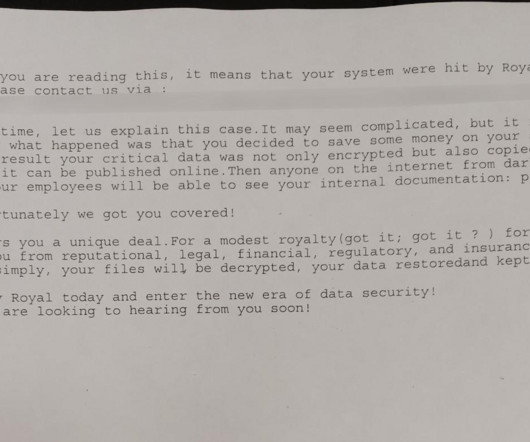
Avoslocker ransomware gang targets US critical infrastructure
Security Affairs
MARCH 19, 2022
Implement network segmentation and maintain offline backups of data to ensure limited interruption to the organization. Regularly back up data, password protect backup copies offline. Install and regularly update antivirus software on all hosts, and enable real time detection. Avoid reusing passwords for multiple accounts.

































Let's personalize your content