ALPHV/BlackCat ransomware affiliate targets Veritas Backup solution bugs
Security Affairs
APRIL 4, 2023
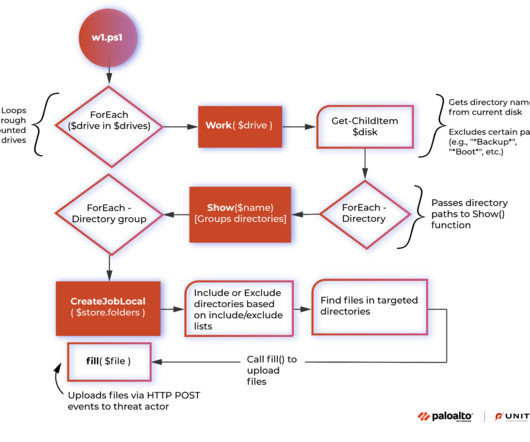
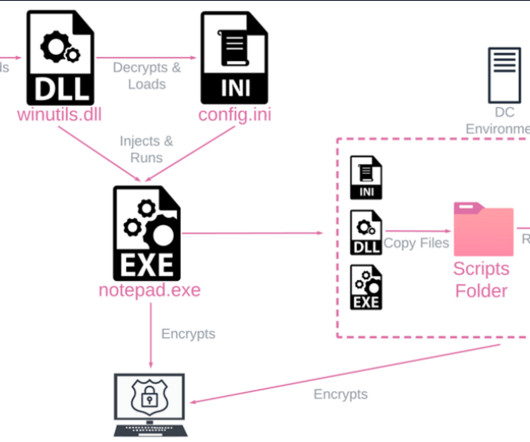
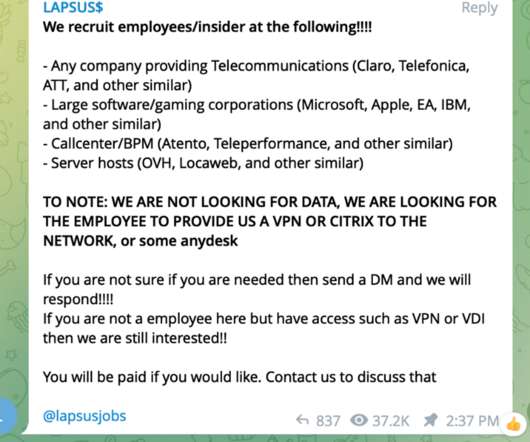
An ALPHV/BlackCat ransomware affiliate was spotted exploiting vulnerabilities in the Veritas Backup solution. An affiliate of the ALPHV/BlackCat ransomware gang, tracked as UNC4466, was observed exploiting three vulnerabilities in the Veritas Backup solution to gain initial access to the target network. CVSS score: 8.1).









































Let's personalize your content