Security Resilience in APJC
Cisco Security
JULY 19, 2022
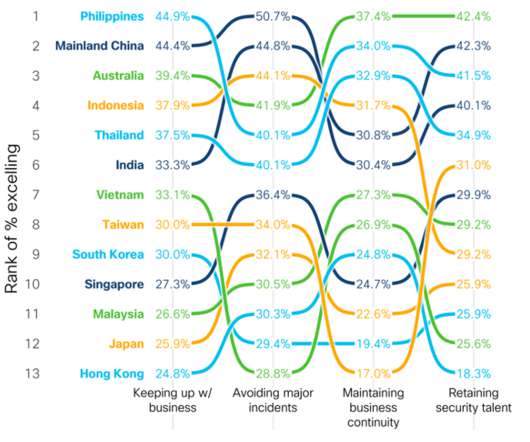
As the world continues to face formidable challenges, one of the many things impacted is cybersecurity. Lately we’ve been talking a lot about security resilience , and how companies can embrace it to stay the course no matter what happens. Security performance across the region.




















Let's personalize your content