What Is Integrated Risk Management? Definition & Implementation
eSecurity Planet
APRIL 29, 2024
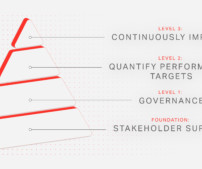
These include new opportunities, clear priorities, and better security, performance, and resilience. The values provide clear and justifiable prioritization easily communicated throughout the organization to align goals for operations, security, and finance.











Let's personalize your content